测试postman中OAuth2提供者endpoint的简单实现
我已经从github下载了SpringSecurity OAuth2测试代码,并通过运行主应用程序类启动了vanilla服务器。
来自Spring文档:
框架提供的URL路径是/oauth/authorize(授权endpoint)、/oauth/token(令牌endpoint)
我想用postman测试这两个endpoint,模拟客户端凭据授予流。但是,如果我尝试使用基本Auth访问这些endpoint,例如https://localhost:8083/oauth/authorize,给出用户名“user”和密码“password”,我会得到“访问此资源需要完全身份验证”。
package demo;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.context.annotation.Configuration;
import org.springframework.http.HttpStatus;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerSecurityConfigurer;
import org.springframework.util.MultiValueMap;
import org.springframework.web.bind.annotation.RequestBody;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RequestMethod;
import org.springframework.web.bind.annotation.ResponseStatus;
import org.springframework.web.bind.annotation.RestController;
@SpringBootApplication
@EnableResourceServer
@RestController
public class Application {
public static void main(String[] args) {
SpringApplication.run(Application.class, args);
}
@RequestMapping("/")
public String home() {
return "Hello World";
}
@RequestMapping(value = "/", method = RequestMethod.POST)
@ResponseStatus(HttpStatus.CREATED)
public String create(@RequestBody MultiValueMap<String, String> map) {
return "OK";
}
@Configuration
@EnableAuthorizationServer
protected static class OAuth2Config extends AuthorizationServerConfigurerAdapter {
@Autowired
private AuthenticationManager authenticationManager;
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception {
endpoints.authenticationManager(authenticationManager);
}
@Override
public void configure(AuthorizationServerSecurityConfigurer security) throws Exception {
security.checkTokenAccess("isAuthenticated()");
}
@Override
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
// @formatter:off
clients.inMemory()
.withClient("myapp")
.secret("myappsecret")
.resourceIds("myresources")
.authorizedGrantTypes("client_credentials","refresh_token")
.authorities("USER")
.scopes("read", "write", "trust")
.accessTokenValiditySeconds(3000)
.refreshTokenValiditySeconds(3000)
.and()
.withClient("my-trusted-client")
.authorizedGrantTypes("password", "authorization_code", "refresh_token", "implicit")
.authorities("ROLE_CLIENT", "ROLE_TRUSTED_CLIENT")
.scopes("read", "write", "trust")
.resourceIds("oauth2-resource")
.accessTokenValiditySeconds(600)
.redirectUris("http://anywhere")
.and()
.withClient("my-client-with-registered-redirect")
.authorizedGrantTypes("authorization_code")
.authorities("ROLE_CLIENT")
.scopes("read", "trust")
.resourceIds("oauth2-resource")
.redirectUris("http://anywhere?key=value")
.and()
.withClient("my-client-with-secret")
.authorizedGrantTypes("client_credentials", "password")
.authorities("ROLE_CLIENT")
.scopes("read")
.resourceIds("oauth2-resource")
.secret("secret");
// @formatter:on
}
}
}
application.yml
spring:
application:
name: vanilla
management:
context_path: /admin
security:
user:
password: password
oauth2:
resource:
filter-order: 3
server:
port: 8083
logging:
level:
org.springframework.security: WARN
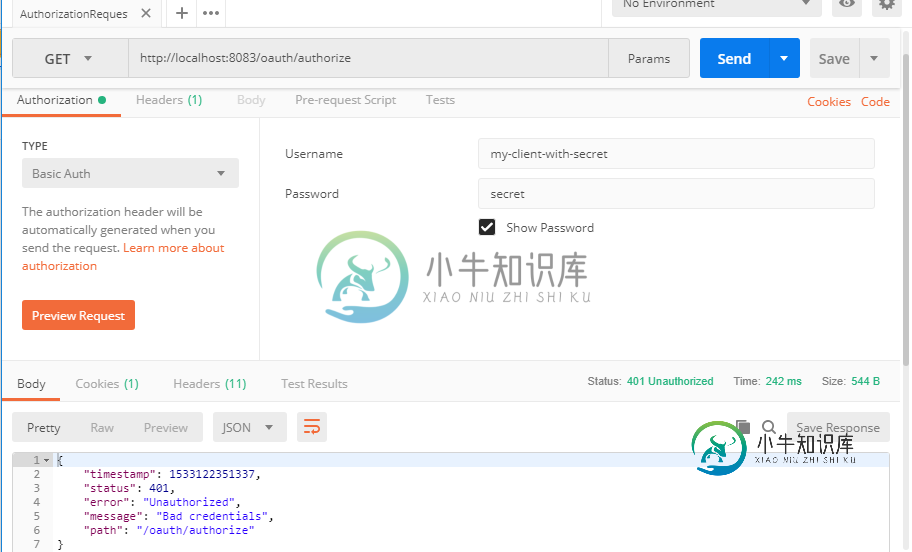
服务器日志:
2018-08-01 08:25:24.166 INFO 18524 --- [ main] s.b.c.e.t.TomcatEmbeddedServletContainer : Tomcat started on port(s): 8083 (http)
2018-08-01 08:25:24.172 INFO 18524 --- [ main] demo.Application : Started Application in 6.514 seconds (JVM running for 7.163)
2018-08-01 08:25:41.709 INFO 18524 --- [nio-8083-exec-2] o.a.c.c.C.[Tomcat].[localhost].[/] : Initializing Spring FrameworkServlet 'dispatcherServlet'
2018-08-01 08:25:41.709 INFO 18524 --- [nio-8083-exec-2] o.s.web.servlet.DispatcherServlet : FrameworkServlet 'dispatcherServlet': initialization started
2018-08-01 08:25:41.761 INFO 18524 --- [nio-8083-exec-2] o.s.web.servlet.DispatcherServlet : FrameworkServlet 'dispatcherServlet': initialization completed in 52 ms
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/css/**']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/css/**'
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/js/**']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/js/**'
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/images/**']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/images/**'
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/webjars/**']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/webjars/**'
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/**/favicon.ico']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/**/favicon.ico'
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/error']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/error'
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : No matches found
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/oauth/token']
2018-08-01 08:25:41.791 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/oauth/token'
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/oauth/token_key']
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/oauth/token_key'
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/oauth/check_token']
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/oauth/check_token'
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : No matches found
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/admin/**'
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/**']
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Request '/oauth/authorize' matched by universal pattern '/**'
2018-08-01 08:25:41.792 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : matched
2018-08-01 08:25:41.793 DEBUG 18524 --- [nio-8083-exec-2] o.s.security.web.FilterChainProxy : /oauth/authorize at position 1 of 11 in additional filter chain; firing Filter: 'WebAsyncManagerIntegrationFilter'
2018-08-01 08:25:41.794 DEBUG 18524 --- [nio-8083-exec-2] o.s.security.web.FilterChainProxy : /oauth/authorize at position 2 of 11 in additional filter chain; firing Filter: 'SecurityContextPersistenceFilter'
2018-08-01 08:25:41.797 DEBUG 18524 --- [nio-8083-exec-2] o.s.security.web.FilterChainProxy : /oauth/authorize at position 3 of 11 in additional filter chain; firing Filter: 'HeaderWriterFilter'
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.header.writers.HstsHeaderWriter : Not injecting HSTS header since it did not match the requestMatcher org.springframework.security.web.header.writers.HstsHeaderWriter$SecureRequestMatcher@c3dc28b
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.security.web.FilterChainProxy : /oauth/authorize at position 4 of 11 in additional filter chain; firing Filter: 'LogoutFilter'
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/logout', GET]
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Checking match of request : '/oauth/authorize'; against '/logout'
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/logout', POST]
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Request 'GET /oauth/authorize' doesn't match 'POST /logout
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/logout', PUT]
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Request 'GET /oauth/authorize' doesn't match 'PUT /logout
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : Trying to match using Ant [pattern='/logout', DELETE]
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.u.matcher.AntPathRequestMatcher : Request 'GET /oauth/authorize' doesn't match 'DELETE /logout
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.web.util.matcher.OrRequestMatcher : No matches found
2018-08-01 08:25:41.798 DEBUG 18524 --- [nio-8083-exec-2] o.s.security.web.FilterChainProxy : /oauth/authorize at position 5 of 11 in additional filter chain; firing Filter: 'BasicAuthenticationFilter'
2018-08-01 08:25:41.800 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.a.www.BasicAuthenticationFilter : Basic Authentication Authorization header found for user 'my-client-with-secret'
2018-08-01 08:25:41.801 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.authentication.ProviderManager : Authentication attempt using org.springframework.security.authentication.dao.DaoAuthenticationProvider
2018-08-01 08:25:41.803 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.a.dao.DaoAuthenticationProvider : User 'my-client-with-secret' not found
2018-08-01 08:25:41.805 DEBUG 18524 --- [nio-8083-exec-2] o.s.s.w.a.www.BasicAuthenticationFilter : Authentication request for failed: org.springframework.security.authentication.BadCredentialsException: Bad credentials
2018-08-01 08:25:41.805 DEBUG 18524 --- [nio-8083-exec-2] s.s.w.c.SecurityContextPersistenceFilter : SecurityContextHolder now cleared, as request processing completed
共有1个答案
这可以帮到某人。
使用OAuth2.0授权测试API
- 打开授权选项卡。
-
我刚刚开始对我的系统采用Pact测试,它由一个提供者服务和一个作为消费者的棱角前端组成。我成功地设置了双方,因此,Angular应用程序生成了一个(单个)pact文件,与我的提供者服务的多个endpoint进行了许多交互。在提供程序中,我现在确实面临这样一个问题,即我的验证测试变得非常庞大和过于复杂,因为我必须在一个测试中用所有endpoint的数据模拟所有endpoint,例如: 有没有一种方法
-
令牌名称:mytoken Auth URL:localhost:8080/admin/oauth 访问令牌URL:localhost:8080/admin/oauth/Token
-
问题内容: 我指的是“ 有效Java ”的第2章中讨论的“服务提供者框架” ,这似乎是解决我遇到的问题的正确方法,其中我需要在运行时实例化几个类之一,并根据选择一个服务和一个对象(基本上是XML代码段): 但是,如何让各个服务提供者(例如,一堆默认提供者+一些自定义提供者)进行注册? 例如,如果我编写了自定义类MyFooAlgorithm和MyFooAlgorithmProvider来实现FooA
-
简介 FuelPHP 核心有几个预安装的提供者套件。预安装套件是来自外部各方的函式库, 被整合进 FuelPHP 核心。 预安装套件 htmLawed,版本 1.1.12 markdown_extra,版本 1.0.1(markdown)和 1.2.5(markdown_extra) PHPQuickProfiler PHPSecLib,版本 0.2.2 spyc,版本 0.5
-
我们有两个服务,其中一个是另一个的消费者。使用者是用Java编写的,提供者是用JavaScript编写的。 在消费者端,我们使用pact-jvm定义了一个consumer-contract-test,并且能够生成一个合同。在此契约中,响应的定义如下: 用于pact验证的代码 有什么办法解决这个问题吗?是否可能在消费者端使用带有内容键的类似消息结构?或者我们可以在提供方用其他方法解决它吗
-
我试图授权用户使用Oauth2从我的Django REST框架API访问一些资源。 大多数关于Oau2和API的答案都涉及使API成为提供者。 但是我打算和很多REST APIs共用一个Oauth2提供者,想不通怎么消费(不是怎么提供Oauth2)。 我不知道用户如何登录提供程序 SSO,然后将其令牌传送到我的消费 API,该 API 必须针对我的提供程序对用户进行身份验证(获取其信息,主要是授权

