kube-score
kube-score is a tool that performs static code analysis of your Kubernetes object definitions.
The output is a list of recommendations of what you can improve to make your application more secure and resilient.
You can test kube-score out in the browser with the online demo (source).
Installation
kube-score is easy to install, and is available from the following sources:
| Distribution | Command / Link |
|---|---|
| Pre-built binaries for macOS, Linux, and Windows | GitHub releases |
| Docker | docker pull zegl/kube-score (Docker Hub) |
| Homebrew (macOS and Linux) | brew install kube-score/tap/kube-score |
| Krew (macOS and Linux) | kubectl krew install score |
Checks
For a full list of checks, see README_CHECKS.md.
- Container limits (should be set)
- Pod is targeted by a
NetworkPolicy, both egress and ingress rules are recommended - Deployments and StatefulSets should have a
PodDisruptionPolicy - Deployments and StatefulSets should have host PodAntiAffinity configured
- Container probes, a readiness should be configured, and should not be identical to the liveness probe. Read more in README_PROBES.md.
- Container securityContext, run as high number user/group, do not run as root or with privileged root fs. Read more in README_SECURITYCONTEXT.md.
- Stable APIs, use a stable API if available (supported: Deployments, StatefulSets, DaemonSet)
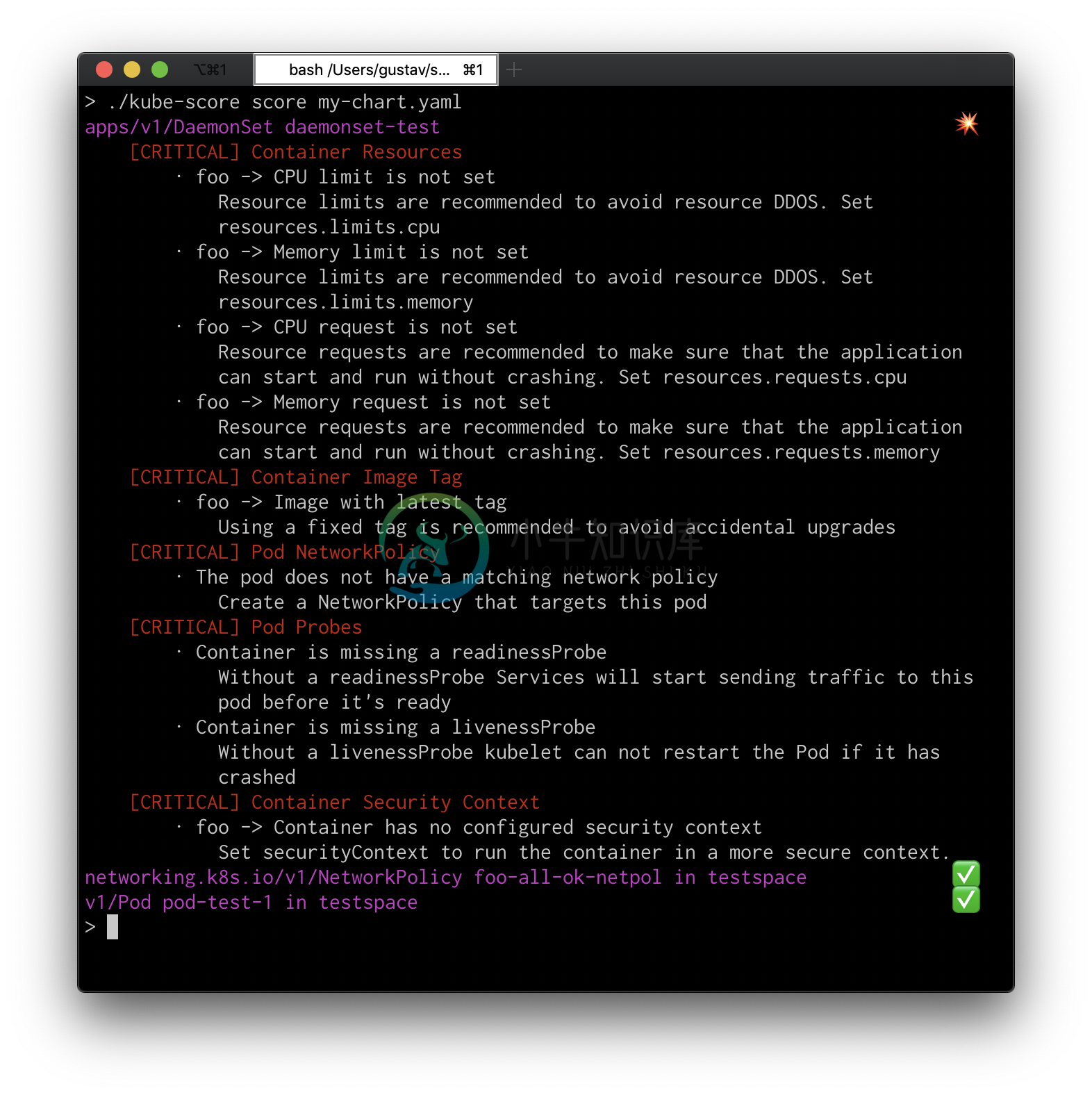
Example output
Usage in CI
kube-score can run in your CI/CD environment and will exit with exit code 1 if a critical error has been found.The trigger level can be changed to warning with the --exit-one-on-warning argument.
The input to kube-score should be all applications that you deploy to the same namespace for the best result.
Example with Helm
helm template my-app | kube-score score -
Example with Kustomize
kustomize build . | kube-score score -
Example with static YAMLs
kube-score score my-app/*.yaml
kube-score score my-app/deployment.yaml my-app/service.yaml
Example with an existing cluster
kubectl api-resources --verbs=list --namespaced -o name \
| xargs -n1 -I{} bash -c "kubectl get {} --all-namespaces -oyaml && echo ---" \
| kube-score score -
Example with Docker
docker run -v $(pwd):/project zegl/kube-score:v1.10.0 score my-app/*.yaml
Configuration
Usage of kube-score:
kube-score [action] --flags
Actions:
score Checks all files in the input, and gives them a score and recommendations
list Prints a CSV list of all available score checks
version Print the version of kube-score
help Print this message
Flags for score:
--disable-ignore-checks-annotations Set to true to disable the effect of the 'kube-score/ignore' annotations
--enable-optional-test strings Enable an optional test, can be set multiple times
--exit-one-on-warning Exit with code 1 in case of warnings
--help Print help
--ignore-container-cpu-limit Disables the requirement of setting a container CPU limit
--ignore-container-memory-limit Disables the requirement of setting a container memory limit
--ignore-test strings Disable a test, can be set multiple times
--kubernetes-version string Setting the kubernetes-version will affect the checks ran against the manifests. Set this to the version of Kubernetes that you're using in production for the best results. (default "v1.18")
-o, --output-format string Set to 'human', 'json' or 'ci'. If set to ci, kube-score will output the program in a format that is easier to parse by other programs. (default "human")
--output-version string Changes the version of the --output-format. The 'json' format has version 'v2' (default) and 'v1' (deprecated, will be removed in v1.7.0). The 'human' and 'ci' formats has only version 'v1' (default). If not explicitly set, the default version for that particular output format will be used.
-v, --verbose count Enable verbose output, can be set multiple times for increased verbosity.
Ignoring a test
Tests can be ignored in the whole run of the program, with the --ignore-test flag.
A test can also be ignored on a per-object basis, by adding the annotation kube-score/ignore to the object.The value should be a comma separated string of the test IDs.
Example:
Testing this object will temporarily disable the service-type test, which warns against using services of type NodePort.
apiVersion: v1
kind: Service
metadata:
name: node-port-service-with-ignore
namespace: foospace
annotations:
kube-score/ignore: service-type
spec:
selector:
app: my-app
ports:
- protocol: TCP
port: 80
targetPort: 8080
type: NodePort
Building from source
kube-score requires Go 1.11 or later to build. Clone this repository, and then:
# Build the project
go build github.com/zegl/kube-score/cmd/kube-score
# Run all tests
go test -v github.com/zegl/kube-score/...
Contributing?
Do you want to help out? Take a look at the Contributing Guidelines for more info.
-
kube-scheduler是k8s的一个核心组件,其主要功能是为刚创建的pod(nodename为空)选择一个合适的node。 工作流程大概为:kube-scheduler会使用informer机制监听pod资源变化(除了监听pod,也会监听node, pv等,这里先关注pod),如果发现pod的pod.Spec.NodeName字段为空,表示此pod还没有被分配node(如果用户指定pod.S
-
scheduler配置与源码分析 配置参数 启动参数 在kubernetes中,组件的配置文件格式都推荐使用yaml格式,scheduler也不例外。下面是scheduler启动时所需要的全局配置类。 // scheduler的全局配置 type Options struct { // The default values. These are overridden if ConfigFile
-
前言 kube-scheduler基于Kubernetes管理的资源(比如CPU、内存、PV等)进行调度,但是,当需要对在Kubernetes外部管理的资源进行调度时,在Extender之前没有任何机制可以做到这一点。有一种方法可以让kubernetes具有扩展性,就是增加HTTP调度扩展程序。 有三种方法可以向kube-scheduler添加新的调度规则: 更新现有的或添加新的调度插件并重新编译
-
Version: Kubernetes 1.13 前言 Kubernetes每个Node上运行Kube-proxy做网络代理,用来实现Kubernetes中的service与pod之间的流量转发。本文将对Kube-Proxy的源码进行阅读,看看Kube-Proxy具体的实现逻辑。 其中关于Kube-Proxy的实现原理可以参考: https://kubernetes.io/docs/concept
-
调度框架用来保存配置的插件,并在调度算法中被执行遍历插件,其实现了如下接口 type Framework interface { //提供了插件获取调度框架里数据的接口和抢占接口,见下面注释 Handle //返回排序函数,用在调度队列中,用来给pod排序 QueueSortFunc() LessFunc //用来执行配置的PreFilter插件 RunPreFilterPlugi
-
kubernetes 1.12.1版本 Desc The Kubernetes network proxy runs on each node. This reflects services as defined in the Kubernetes API on each node and can do simple TCP, UDP, and SCTP stream forwar
-
Kube 足够的简单,足够小,具有很强的自适应能力,是个响应式的 CSS 框架。它拥有最新最炫的网格和漂亮的字体排版,没有任何样式绑定,给用户以绝对的自由。 支持的浏览器包括: Latest Chrome Latest Firefox Latest Safari Latest Opera IE 8+ 手机浏览器
-
Kube-OVN 将基于 OVN/OVS 的网络虚拟化方案带入 Kubernetes,提供了针对企业应用场景的高级容器网络编排功能。 主要功能: 基于Namespace的子网划分,以及网络控制 容器固定 IP IPv6支持 细粒度网络策略 动态 QoS 分布式和集中式网关 内嵌负载均衡器 支持集群内外网络直通 控制平面的灾备及高可用 丰富的监控和链路追踪工具 未来计划: 基于 XDP/DPDK/O
-
kube-eventer 是一个事件发射器,它将 Kubernetes 事件发送到接收器(例如,DingTalk、SLS、Kafka 等)。 监控是保障系统稳定性的重要组成部分,在 Kubernetes 开源生态中,资源类的监控工具与组件百花齐放,但是,只有资源类的监控是远远不够的,因为资源监控存在如下两个主要的缺欠: 监控的实时性与准确性不足 监控的场景覆盖范围不足 Kubernetes 的核心
-
kube-backup Quick 'n dirty kubernetes state backup script, designed to be ran as kubernetes Job. Think of it like RANCID for kubernetes. Props to @gianrubio for coming up with the idea. Setup Use the
-
kube-ps1: Kubernetes prompt for bash and zsh A script that lets you add the current Kubernetes context and namespaceconfigured on kubectl to your Bash/Zsh prompt strings (i.e. the $PS1). Inspired by s
-
�� Provision a Kubernetes / CoreOS Cluster on Linode Automatically provision a scalable CoreOS/Kubernetes cluster on Linode with zero configuration. The cluster will comprise of a single Kubernetes ma