Spring Cloud Kubernetes
- 1. Why do you need Spring Cloud Kubernetes?
- 2. Starters
- 3. DiscoveryClient for Kubernetes
- 4. Kubernetes native service discovery
- 5. Kubernetes PropertySource implementations
- 6. Kubernetes Ecosystem Awareness
- 7. Pod Health Indicator
- 8. Info Contributor
- 9. Leader Election
- 10. LoadBalancer for Kubernetes
- 11. Security Configurations Inside Kubernetes
- 12. Service Registry Implementation
- 13. Spring Cloud Kubernetes Configuration Watcher
- 14. Examples
- 15. Other Resources
- 16. Configuration properties
- 17. Building
- 18. Contributing
This reference guide covers how to use Spring Cloud Kubernetes.
1. Why do you need Spring Cloud Kubernetes?
Spring Cloud Kubernetes provides implementations of well known Spring Cloud interfaces allowing developers to build and run Spring Cloud applications on Kubernetes. While this project may be useful to you when building a cloud native application, it is also not a requirement in order to deploy a Spring Boot app on Kubernetes. If you are just getting started in your journey to running your Spring Boot app on Kubernetes you can accomplish a lot with nothing more than a basic Spring Boot app and Kubernetes itself. To learn more, you can get started by reading the Spring Boot reference documentation for deploying to Kubernetes and also working through the workshop material Spring and Kubernetes.
2. Starters
Starters are convenient dependency descriptors you can include in yourapplication. Include a starter to get the dependencies and Spring Bootauto-configuration for a feature set. Starters that begin with spring-cloud-starter-kubernetes-fabric8provide implementations using the Fabric8 Kubernetes Java Client.Starters that begin withspring-cloud-starter-kubernetes-client provide implementations using the Kubernetes Java Client.
| Starter | Features |
|---|---|
|
Fabric8 Dependency
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-fabric8</artifactId>
</dependency>
Kubernetes Client Dependency
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-client</artifactId>
</dependency>
|
Discovery Client implementation thatresolves service names to Kubernetes Services. |
|
Fabric8 Dependency
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-fabric8-config</artifactId>
</dependency>
Kubernetes Client Dependency
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-client-config</artifactId>
</dependency>
|
Load application properties from KubernetesConfigMaps and Secrets.Reload application properties when a ConfigMap orSecret changes. |
|
Fabric8 Dependency
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-fabric8-all</artifactId>
</dependency>
Kubernetes Client Dependency
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-client-all</artifactId>
</dependency>
|
All Spring Cloud Kubernetes features. |
3. DiscoveryClient for Kubernetes
This project provides an implementation of Discovery Clientfor Kubernetes.This client lets you query Kubernetes endpoints (see services) by name.A service is typically exposed by the Kubernetes API server as a collection of endpoints that represent http and https addresses and that a client canaccess from a Spring Boot application running as a pod.
This is something that you get for free by adding the following dependency inside your project:
Fabric8 Kubernetes Client
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-fabric8</artifactId>
</dependency>
Kubernetes Java Client
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-client</artifactId>
</dependency>
To enable loading of the DiscoveryClient, add @EnableDiscoveryClient to the according configuration or application class, as the following example shows:
@SpringBootApplication
@EnableDiscoveryClient
public class Application {
public static void main(String[] args) {
SpringApplication.run(Application.class, args);
}
}
Then you can inject the client in your code simply by autowiring it, as the following example shows:
@Autowired
private DiscoveryClient discoveryClient;
You can choose to enable DiscoveryClient from all namespaces by setting the following property in application.properties:
spring.cloud.kubernetes.discovery.all-namespaces=trueTo discover service endpoint addresses that are not marked as "ready" by the kubernetes api server, you can set the following property in application.properties (default: false):
spring.cloud.kubernetes.discovery.include-not-ready-addresses=true|
Note
|
This might be useful when discovering services for monitoring purposes, and would enable inspecting the /health endpoint of not-ready service instances. |
If your service exposes multiple ports, you will need to specify which port the DiscoveryClient should use.The DiscoveryClient will choose the port using the following logic.
If the service has a label
primary-port-nameit will use the port with the name specified in the label’s value.If no label is present, then the port name specified in
spring.cloud.kubernetes.discovery.primary-port-namewill be used.If neither of the above are specified it will use the port named
https.If none of the above conditions are met it will use the port named
http.As a last resort it wil pick the first port in the list of ports.
|
Warning
|
The last option may result in non-deterministic behaviour.Please make sure to configure your service and/or application accordingly. |
By default all of the ports and their names will be added to the metadata of the ServiceInstance.
If, for any reason, you need to disable the DiscoveryClient, you can set the following property in application.properties:
spring.cloud.kubernetes.discovery.enabled=falseSome Spring Cloud components use the DiscoveryClient in order to obtain information about the local service instance. Forthis to work, you need to align the Kubernetes service name with the spring.application.name property.
|
Note
|
spring.application.name has no effect as far as the name registered for the application within Kubernetes |
Spring Cloud Kubernetes can also watch the Kubernetes service catalog for changes and update theDiscoveryClient implementation accordingly. In order to enable this functionality you need to add@EnableScheduling on a configuration class in your application.
4. Kubernetes native service discovery
Kubernetes itself is capable of (server side) service discovery (see: kubernetes.io/docs/concepts/services-networking/service/#discovering-services).Using native kubernetes service discovery ensures compatibility with additional tooling, such as Istio (istio.io), a service mesh that is capable of load balancing, circuit breaker, failover, and much more.
The caller service then need only refer to names resolvable in a particular Kubernetes cluster. A simple implementation might use a spring RestTemplate that refers to a fully qualified domain name (FQDN), such as {service-name}.{namespace}.svc.{cluster}.local:{service-port}.
Additionally, you can use Hystrix for:
Circuit breaker implementation on the caller side, by annotating the spring boot application class with
@EnableCircuitBreakerFallback functionality, by annotating the respective method with
@HystrixCommand(fallbackMethod=
5. Kubernetes PropertySource implementations
The most common approach to configuring your Spring Boot application is to create an application.properties or application.yaml oran application-profile.properties or application-profile.yaml file that contains key-value pairs that provide customization values to yourapplication or Spring Boot starters. You can override these properties by specifying system properties or environmentvariables.
5.1. Using a ConfigMap PropertySource
Kubernetes provides a resource named ConfigMap to externalize theparameters to pass to your application in the form of key-value pairs or embedded application.properties or application.yaml files.The Spring Cloud Kubernetes Config project makes Kubernetes ConfigMap instances availableduring application bootstrapping and triggers hot reloading of beans or Spring context when changes are detected onobserved ConfigMap instances.
The default behavior is to create a Fabric8ConfigMapPropertySource based on a Kubernetes ConfigMap that has a metadata.name value of either the name ofyour Spring application (as defined by its spring.application.name property) or a custom name defined within thebootstrap.properties file under the following key: spring.cloud.kubernetes.config.name.
However, more advanced configuration is possible where you can use multiple ConfigMap instances.The spring.cloud.kubernetes.config.sources list makes this possible.For example, you could define the following ConfigMap instances:
spring:
application:
name: cloud-k8s-app
cloud:
kubernetes:
config:
name: default-name
namespace: default-namespace
sources:
# Spring Cloud Kubernetes looks up a ConfigMap named c1 in namespace default-namespace
- name: c1
# Spring Cloud Kubernetes looks up a ConfigMap named default-name in whatever namespace n2
- namespace: n2
# Spring Cloud Kubernetes looks up a ConfigMap named c3 in namespace n3
- namespace: n3
name: c3
In the preceding example, if spring.cloud.kubernetes.config.namespace had not been set,the ConfigMap named c1 would be looked up in the namespace that the application runs.See Namespace resolution to get a better understanding of how the namespaceof the application is resolved.
Any matching ConfigMap that is found is processed as follows:
Apply individual configuration properties.
Apply as
yamlthe content of any property namedapplication.yaml.Apply as a properties file the content of any property named
application.properties.
The single exception to the aforementioned flow is when the ConfigMap contains a single key that indicatesthe file is a YAML or properties file. In that case, the name of the key does NOT have to be application.yaml orapplication.properties (it can be anything) and the value of the property is treated correctly.This features facilitates the use case where the ConfigMap was created by using something like the following:
kubectl create configmap game-config --from-file=/path/to/app-config.yamlAssume that we have a Spring Boot application named demo that uses the following properties to read its thread poolconfiguration.
pool.size.corepool.size.maximum
This can be externalized to config map in yaml format as follows:
kind: ConfigMap
apiVersion: v1
metadata:
name: demo
data:
pool.size.core: 1
pool.size.max: 16
Individual properties work fine for most cases. However, sometimes, embedded yaml is more convenient. In this case, weuse a single property named application.yaml to embed our yaml, as follows:
kind: ConfigMap
apiVersion: v1
metadata:
name: demo
data:
application.yaml: |-
pool:
size:
core: 1
max:16
The following example also works:
kind: ConfigMap
apiVersion: v1
metadata:
name: demo
data:
custom-name.yaml: |-
pool:
size:
core: 1
max:16
You can also configure Spring Boot applications differently depending on active profiles that are merged togetherwhen the ConfigMap is read. You can provide different property values for different profiles by using anapplication.properties or application.yaml property, specifying profile-specific values, each in their own document(indicated by the --- sequence), as follows:
kind: ConfigMap
apiVersion: v1
metadata:
name: demo
data:
application.yml: |-
greeting:
message: Say Hello to the World
farewell:
message: Say Goodbye
---
spring:
profiles: development
greeting:
message: Say Hello to the Developers
farewell:
message: Say Goodbye to the Developers
---
spring:
profiles: production
greeting:
message: Say Hello to the Ops
In the preceding case, the configuration loaded into your Spring Application with the development profile is as follows:
greeting:
message: Say Hello to the Developers
farewell:
message: Say Goodbye to the Developers
However, if the production profile is active, the configuration becomes:
greeting:
message: Say Hello to the Ops
farewell:
message: Say Goodbye
If both profiles are active, the property that appears last within the ConfigMap overwrites any preceding values.
Another option is to create a different config map per profile and spring boot will automatically fetch it basedon active profiles
kind: ConfigMap
apiVersion: v1
metadata:
name: demo
data:
application.yml: |-
greeting:
message: Say Hello to the World
farewell:
message: Say Goodbye
kind: ConfigMap
apiVersion: v1
metadata:
name: demo-development
data:
application.yml: |-
spring:
profiles: development
greeting:
message: Say Hello to the Developers
farewell:
message: Say Goodbye to the Developers
kind: ConfigMap
apiVersion: v1
metadata:
name: demo-production
data:
application.yml: |-
spring:
profiles: production
greeting:
message: Say Hello to the Ops
farewell:
message: Say Goodbye
To tell Spring Boot which profile should be enabled at bootstrap, you can pass SPRING_PROFILES_ACTIVE environment variable. To do so, you can launch your Spring Boot application with an environment variable that you can define it in the PodSpec at the container specification. Deployment resource file, as follows:
apiVersion: apps/v1
kind: Deployment
metadata:
name: deployment-name
labels:
app: deployment-name
spec:
replicas: 1
selector:
matchLabels:
app: deployment-name
template:
metadata:
labels:
app: deployment-name
spec:
containers:
- name: container-name
image: your-image
env:
- name: SPRING_PROFILES_ACTIVE
value: "development"
You could run into a situation where there are multiple configs maps that have the same property names. For example:
kind: ConfigMap
apiVersion: v1
metadata:
name: config-map-one
data:
application.yml: |-
greeting:
message: Say Hello from one
and
kind: ConfigMap
apiVersion: v1
metadata:
name: config-map-two
data:
application.yml: |-
greeting:
message: Say Hello from two
Depending on the order in which you place these in bootstrap.yaml|properties, you might end up with an un-expected result (the last config map wins). For example:
spring:
application:
name: cloud-k8s-app
cloud:
kubernetes:
config:
namespace: default-namespace
sources:
- name: config-map-two
- name: config-map-one
will result in property greetings.message being Say Hello from one.
There is a way to change this default configuration by specifying useNameAsPrefix. For example:
spring:
application:
name: with-prefix
cloud:
kubernetes:
config:
useNameAsPrefix: true
namespace: default-namespace
sources:
- name: config-map-one
useNameAsPrefix: false
- name: config-map-two
Such a configuration will result in two properties being generated:
greetings.messageequal toSay Hello from one.config-map-two.greetings.messageequal toSay Hello from two
Notice that spring.cloud.kubernetes.config.useNameAsPrefix has a lower priority than spring.cloud.kubernetes.config.sources.useNameAsPrefix.This allows you to set a "default" strategy for all sources, at the same time allowing to override only a few.
If using the config map name is not an option, you can specify a different strategy, called : explicitPrefix. Since this is an explicit prefix thatyou select, it can only be supplied to the sources level. At the same time it has a higher priority than useNameASPrefix. Let’s suppose we have a third config map with these entries:
kind: ConfigMap
apiVersion: v1
metadata:
name: config-map-three
data:
application.yml: |-
greeting:
message: Say Hello from three
A configuration like the one below:
spring:
application:
name: with-prefix
cloud:
kubernetes:
config:
useNameAsPrefix: true
namespace: default-namespace
sources:
- name: config-map-one
useNameAsPrefix: false
- name: config-map-two
explicitPrefix: two
- name: config-map-three
will result in three properties being generated:
greetings.messageequal toSay Hello from one.two.greetings.messageequal toSay Hello from two.config-map-three.greetings.messageequal toSay Hello from three.
|
Note
|
You should check the security configuration section. To access config maps from inside a pod you need to have the correctKubernetes service accounts, roles and role bindings. |
Another option for using ConfigMap instances is to mount them into the Pod by running the Spring Cloud Kubernetes applicationand having Spring Cloud Kubernetes read them from the file system.This behavior is controlled by the spring.cloud.kubernetes.config.paths property. You can use it inaddition to or instead of the mechanism described earlier.You can specify multiple (exact) file paths in spring.cloud.kubernetes.config.paths by using the , delimiter.
|
Note
|
You have to provide the full exact path to each property file, because directories are not being recursively parsed. |
|
Note
|
If you use spring.cloud.kubernetes.config.paths or spring.cloud.kubernetes.secrets.path the automatic reloadfunctionality will not work. You will need to make a POST request to the /actuator/refresh endpoint orrestart/redeploy the application. |
| Name | Type | Default | Description |
|---|---|---|---|
|
|
|
Enable ConfigMaps |
|
|
|
Sets the name of |
|
|
Client namespace |
Sets the Kubernetes namespace where to lookup |
|
|
|
Sets the paths where |
|
|
|
Enable or disable consuming |
5.2. Secrets PropertySource
Kubernetes has the notion of Secrets for storingsensitive data such as passwords, OAuth tokens, and so on. This project provides integration with Secrets to make secretsaccessible by Spring Boot applications. You can explicitly enable or disable This feature by setting the spring.cloud.kubernetes.secrets.enabled property.
When enabled, the Fabric8SecretsPropertySource looks up Kubernetes for Secrets from the following sources:
Reading recursively from secrets mounts
Named after the application (as defined by
spring.application.name)Matching some labels
Note:
By default, consuming Secrets through the API (points 2 and 3 above) is not enabled for security reasons. The permission 'list' on secrets allows clients to inspect secrets values in the specified namespace.Further, we recommend that containers share secrets through mounted volumes.
If you enable consuming Secrets through the API, we recommend that you limit access to Secrets by using an authorization policy, such as RBAC.For more information about risks and best practices when consuming Secrets through the API refer to this doc.
If the secrets are found, their data is made available to the application.
Assume that we have a spring boot application named demo that uses properties to read its databaseconfiguration. We can create a Kubernetes secret by using the following command:
kubectl create secret generic db-secret --from-literal=username=user --from-literal=password=p455w0rdThe preceding command would create the following secret (which you can see by using kubectl get secrets db-secret -o yaml):
apiVersion: v1
data:
password: cDQ1NXcwcmQ=
username: dXNlcg==
kind: Secret
metadata:
creationTimestamp: 2017-07-04T09:15:57Z
name: db-secret
namespace: default
resourceVersion: "357496"
selfLink: /api/v1/namespaces/default/secrets/db-secret
uid: 63c89263-6099-11e7-b3da-76d6186905a8
type: Opaque
Note that the data contains Base64-encoded versions of the literal provided by the create command.
Your application can then use this secret — for example, by exporting the secret’s value as environment variables:
apiVersion: v1
kind: Deployment
metadata:
name: ${project.artifactId}
spec:
template:
spec:
containers:
- env:
- name: DB_USERNAME
valueFrom:
secretKeyRef:
name: db-secret
key: username
- name: DB_PASSWORD
valueFrom:
secretKeyRef:
name: db-secret
key: password
You can select the Secrets to consume in a number of ways:
By listing the directories where secrets are mapped:
-Dspring.cloud.kubernetes.secrets.paths=/etc/secrets/db-secret,etc/secrets/postgresql
If you have all the secrets mapped to a common root, you can set them like:
-Dspring.cloud.kubernetes.secrets.paths=/etc/secrets
By setting a named secret:
-Dspring.cloud.kubernetes.secrets.name=db-secret
By defining a list of labels:
-Dspring.cloud.kubernetes.secrets.labels.broker=activemq -Dspring.cloud.kubernetes.secrets.labels.db=postgresql
As the case with ConfigMap, more advanced configuration is also possible where you can use multiple Secretinstances. The spring.cloud.kubernetes.secrets.sources list makes this possible.For example, you could define the following Secret instances:
spring:
application:
name: cloud-k8s-app
cloud:
kubernetes:
secrets:
name: default-name
namespace: default-namespace
sources:
# Spring Cloud Kubernetes looks up a Secret named s1 in namespace default-namespace
- name: s1
# Spring Cloud Kubernetes looks up a Secret named default-name in namespace n2
- namespace: n2
# Spring Cloud Kubernetes looks up a Secret named s3 in namespace n3
- namespace: n3
name: s3
In the preceding example, if spring.cloud.kubernetes.secrets.namespace had not been set,the Secret named s1 would be looked up in the namespace that the application runs.See namespace-resolution to get a better understanding of how the namespaceof the application is resolved.
| Name | Type | Default | Description |
|---|---|---|---|
|
|
|
Enable Secrets |
|
|
|
Sets the name of the secret to look up |
|
|
Client namespace |
Sets the Kubernetes namespace where to look up |
|
|
|
Sets the labels used to lookup secrets |
|
|
|
Sets the paths where secrets are mounted (example 1) |
|
|
|
Enables or disables consuming secrets through APIs (examples 2 and 3) |
Notes:
The
spring.cloud.kubernetes.secrets.labelsproperty behaves as defined byMap-based binding.The
spring.cloud.kubernetes.secrets.pathsproperty behaves as defined byCollection-based binding.Access to secrets through the API may be restricted for security reasons. The preferred way is to mount secrets to the Pod.
You can find an example of an application that uses secrets (though it has not been updated to use the new spring-cloud-kubernetes project) atspring-boot-camel-config
5.3. Namespace resolution
Finding an application namespace happens on a best-effort basis. There are some steps that we iterate in orderto find it. The easiest and most common one, is to specify it in the proper configuration, for example:
spring:
application:
name: app
cloud:
kubernetes:
secrets:
name: secret
namespace: default
sources:
# Spring Cloud Kubernetes looks up a Secret named 'a' in namespace 'default'
- name: a
# Spring Cloud Kubernetes looks up a Secret named 'secret' in namespace 'b'
- namespace: b
# Spring Cloud Kubernetes looks up a Secret named 'd' in namespace 'c'
- namespace: c
name: d
Remember that the same can be done for config maps. If such a namespace is not specified, it will be read (in this order):
from property
spring.cloud.kubernetes.client.namespacefrom a String residing in a file denoted by
spring.cloud.kubernetes.client.serviceAccountNamespacePathpropertyfrom a String residing in
/var/run/secrets/kubernetes.io/serviceaccount/namespacefile(kubernetes default namespace path)from a designated client method call (for example fabric8’s :
KubernetesClient::getNamespace), if the client providessuch a method.
Failure to find a namespace from the above steps will result in an Exception being raised.
5.4. PropertySource Reload
|
Warning
|
This functionality has been deprecated in the 2020.0 release. Please seethe Spring Cloud Kubernetes Configuration Watcher controller for an alternative wayto achieve the same functionality. |
Some applications may need to detect changes on external property sources and update their internal status to reflect the new configuration.The reload feature of Spring Cloud Kubernetes is able to trigger an application reload when a related ConfigMap orSecret changes.
By default, this feature is disabled. You can enable it by using the spring.cloud.kubernetes.reload.enabled=true configuration property (for example, in the application.properties file).
The following levels of reload are supported (by setting the spring.cloud.kubernetes.reload.strategy property):
refresh(default): Only configuration beans annotated with@ConfigurationPropertiesor@RefreshScopeare reloaded.This reload level leverages the refresh feature of Spring Cloud Context.restart_context: the whole SpringApplicationContextis gracefully restarted. Beans are recreated with the new configuration.In order for the restart context functionality to work properly you must enable and expose the restart actuator endpoint
management:
endpoint:
restart:
enabled: true
endpoints:
web:
exposure:
include: restart
shutdown: the SpringApplicationContextis shut down to activate a restart of the container. When you use this level, make sure that the lifecycle of all non-daemon threads is bound to theApplicationContextand that a replication controller or replica set is configured to restart the pod.
Assuming that the reload feature is enabled with default settings (refresh mode), the following bean is refreshed when the config map changes:
@Configuration
@ConfigurationProperties(prefix = "bean")
public class MyConfig {
private String message = "a message that can be changed live";
// getter and setters
}
To see that changes effectively happen, you can create another bean that prints the message periodically, as follows
@Component
public class MyBean {
@Autowired
private MyConfig config;
@Scheduled(fixedDelay = 5000)
public void hello() {
System.out.println("The message is: " + config.getMessage());
}
}
You can change the message printed by the application by using a ConfigMap, as follows:
apiVersion: v1
kind: ConfigMap
metadata:
name: reload-example
data:
application.properties: |-
bean.message=Hello World!
Any change to the property named bean.message in the ConfigMap associated with the pod is reflected in theoutput. More generally speaking, changes associated to properties prefixed with the value defined by the prefixfield of the @ConfigurationProperties annotation are detected and reflected in the application.Associating a ConfigMap with a pod is explained earlier in this chapter.
The full example is available in spring-cloud-kubernetes-reload-example.
The reload feature supports two operating modes:* Event (default): Watches for changes in config maps or secrets by using the Kubernetes API (web socket).Any event produces a re-check on the configuration and, in case of changes, a reload.The view role on the service account is required in order to listen for config map changes. A higher level role (such as edit) is required for secrets(by default, secrets are not monitored).* Polling: Periodically re-creates the configuration from config maps and secrets to see if it has changed.You can configure the polling period by using the spring.cloud.kubernetes.reload.period property and defaults to 15 seconds.It requires the same role as the monitored property source.This means, for example, that using polling on file-mounted secret sources does not require particular privileges.
| Name | Type | Default | Description |
|---|---|---|---|
|
|
|
Enables monitoring of property sources and configuration reload |
|
|
|
Allow monitoring changes in config maps |
|
|
|
Allow monitoring changes in secrets |
|
|
|
The strategy to use when firing a reload ( |
|
|
|
Specifies how to listen for changes in property sources ( |
|
|
|
The period for verifying changes when using the |
Notes:* You should not use properties under spring.cloud.kubernetes.reload in config maps or secrets. Changing such properties at runtime may lead to unexpected results.* Deleting a property or the whole config map does not restore the original state of the beans when you use the refresh level.
6. Kubernetes Ecosystem Awareness
All of the features described earlier in this guide work equally well, regardless of whether your application is running insideKubernetes. This is really helpful for development and troubleshooting.From a development point of view, this lets you start your Spring Boot application and debug oneof the modules that is part of this project. You need not deploy it in Kubernetes,as the code of the project relies on theFabric8 Kubernetes Java client, which is a fluent DSL that cancommunicate by using http protocol to the REST API of the Kubernetes Server.
To disable the integration with Kubernetes you can set spring.cloud.kubernetes.enabled to false. Please be aware that when spring-cloud-kubernetes-config is on the classpath,spring.cloud.kubernetes.enabled should be set in bootstrap.{properties|yml} (or the profile specific one), otherwise it should be in application.{properties|yml} (or the profile specific one).Because of the way we set up a specific EnvironmentPostProcessor in spring-cloud-kubernetes-config, you also need to disable that processor via a system property (or an environment variable), for example you could startyour application via -DSPRING_CLOUD_KUBERNETES_ENABLED=false (any form of relaxed binding will work too).Also note that these properties: spring.cloud.kubernetes.config.enabled and spring.cloud.kubernetes.secrets.enabled only take effect when set in bootstrap.{properties|yml}
6.1. Kubernetes Profile Autoconfiguration
When the application runs as a pod inside Kubernetes, a Spring profile named kubernetes automatically gets activated.This lets you customize the configuration, to define beans that are applied when the Spring Boot application is deployedwithin the Kubernetes platform (for example, different development and production configuration).
6.2. Istio Awareness
When you include the spring-cloud-kubernetes-fabric8-istio module in the application classpath, a new profile is added to the application,provided the application is running inside a Kubernetes Cluster with Istio installed. You can then usespring @Profile("istio") annotations in your Beans and @Configuration classes.
The Istio awareness module uses me.snowdrop:istio-client to interact with Istio APIs, letting us discover traffic rules, circuit breakers, and so on,making it easy for our Spring Boot applications to consume this data to dynamically configure themselves according to the environment.
7. Pod Health Indicator
Spring Boot uses HealthIndicator to expose info about the health of an application.That makes it really useful for exposing health-related information to the user and makes it a good fit for use as readiness probes.
The Kubernetes health indicator (which is part of the core module) exposes the following info:
Pod name, IP address, namespace, service account, node name, and its IP address
A flag that indicates whether the Spring Boot application is internal or external to Kubernetes
You can disable this HealthContributor by setting management.health.kubernetes.enabledto false in application.[properties | yaml].
8. Info Contributor
Spring Cloud Kubernetes includes an InfoContributor which adds Pod information toSpring Boot’s /info Acturator endpoint.
You can disable this InfoContributor by setting management.info.kubernetes.enabledto false in application.[properties | yaml].
9. Leader Election
The Spring Cloud Kubernetes leader election mechanism implements the leader election API of Spring Integration using a Kubernetes ConfigMap.
Multiple application instances compete for leadership, but leadership will only be granted to one.When granted leadership, a leader application receives an OnGrantedEvent application event with leadership Context.Applications periodically attempt to gain leadership, with leadership granted to the first caller.A leader will remain a leader until either it is removed from the cluster, or it yields its leadership.When leadership removal occurs, the previous leader receives OnRevokedEvent application event.After removal, any instances in the cluster may become the new leader, including the old leader.
To include it in your project, add the following dependency.
Fabric8 Leader Implementation
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-kubernetes-fabric8-leader</artifactId>
</dependency>
To specify the name of the configmap used for leader election use the following property.
spring.cloud.kubernetes.leader.config-map-name=leader
10. LoadBalancer for Kubernetes
This project includes Spring Cloud Load Balancer for load balancing based on Kubernetes Endpoints and provides implementation of load balancer based on Kubernetes Service.To include it to your project add the following dependency.
Fabric8 Implementation
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-fabric8-loadbalancer</artifactId>
</dependency>
Kubernetes Java Client Implementation
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-kubernetes-client-loadbalancer</artifactId>
</dependency>
To enable load balancing based on Kubernetes Service name use the following property. Then load balancer would try to call application using address, for example service-a.default.svc.cluster.local
spring.cloud.kubernetes.loadbalancer.mode=SERVICETo enabled load balancing across all namespaces use the following property. Property from spring-cloud-kubernetes-discovery module is respected.
spring.cloud.kubernetes.discovery.all-namespaces=trueIf a service needs to be accessed over HTTPS you need to add a label or annotation to your service definition with the name secured and the value true and the load balancer will then use HTTPS to make requests to the service.
11. Security Configurations Inside Kubernetes
11.1. Namespace
Most of the components provided in this project need to know the namespace. For Kubernetes (1.3+), the namespace is made available to the pod as part of the service account secret and is automatically detected by the client.For earlier versions, it needs to be specified as an environment variable to the pod. A quick way to do this is as follows:
env:
- name: "KUBERNETES_NAMESPACE"
valueFrom:
fieldRef:
fieldPath: "metadata.namespace"11.2. Service Account
For distributions of Kubernetes that support more fine-grained role-based access within the cluster, you need to make sure a pod that runs with spring-cloud-kubernetes has access to the Kubernetes API.For any service accounts you assign to a deployment or pod, you need to make sure they have the correct roles.
Depending on the requirements, you’ll need get, list and watch permission on the following resources:
| Dependency | Resources |
|---|---|
spring-cloud-starter-kubernetes-fabric8 |
pods, services, endpoints |
spring-cloud-starter-kubernetes-fabric8-config |
configmaps, secrets |
spring-cloud-starter-kubernetes-client |
pods, services, endpoints |
spring-cloud-starter-kubernetes-client-config |
configmaps, secrets |
For development purposes, you can add cluster-reader permissions to your default service account. On a production system you’ll likely want to provide more granular permissions.
The following Role and RoleBinding are an example for namespaced permissions for the default account:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: YOUR-NAME-SPACE
name: namespace-reader
rules:
- apiGroups: [""]
resources: ["configmaps", "pods", "services", "endpoints", "secrets"]
verbs: ["get", "list", "watch"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: namespace-reader-binding
namespace: YOUR-NAME-SPACE
subjects:
- kind: ServiceAccount
name: default
apiGroup: ""
roleRef:
kind: Role
name: namespace-reader
apiGroup: ""
12. Service Registry Implementation
In Kubernetes service registration is controlled by the platform, the application itself does not controlregistration as it may do in other platforms. For this reason using spring.cloud.service-registry.auto-registration.enabledor setting @EnableDiscoveryClient(autoRegister=false) will have no effect in Spring Cloud Kubernetes.
13. Spring Cloud Kubernetes Configuration Watcher
Kubernetes provides the ability to mount a ConfigMap or Secret as a volumein the container of your application. When the contents of the ConfigMap or Secret changes, the mounted volume will be updated with those changes.
However, Spring Boot will not automatically update those changes unless you restart the application. Spring Cloudprovides the ability refresh the application context without restarting the application by either hitting theactuator endpoint /refresh or via publishing a RefreshRemoteApplicationEvent using Spring Cloud Bus.
To achieve this configuration refresh of a Spring Cloud app running on Kubernetes, you can deploy the Spring CloudKubernetes Configuration Watcher controller into your Kubernetes cluster.
The application is published as a container and is available on Docker Hub.
Spring Cloud Kubernetes Configuration Watcher can send refresh notifications to applications in two ways.
Over HTTP in which case the application being notified must of the
/refreshactuator endpoint exposed and accessible from within the clusterUsing Spring Cloud Bus, in which case you will need a message broker deployed to your custer for the application to use.
13.1. Deployment YAML
Below is a sample deployment YAML you can use to deploy the Kubernetes Configuration Watcher to Kubernetes.
---
apiVersion: v1
kind: List
items:
- apiVersion: v1
kind: Service
metadata:
labels:
app: spring-cloud-kubernetes-configuration-watcher
name: spring-cloud-kubernetes-configuration-watcher
spec:
ports:
- name: http
port: 8888
targetPort: 8888
selector:
app: spring-cloud-kubernetes-configuration-watcher
type: ClusterIP
- apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app: spring-cloud-kubernetes-configuration-watcher
name: spring-cloud-kubernetes-configuration-watcher
- apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app: spring-cloud-kubernetes-configuration-watcher
name: spring-cloud-kubernetes-configuration-watcher:view
roleRef:
kind: Role
apiGroup: rbac.authorization.k8s.io
name: namespace-reader
subjects:
- kind: ServiceAccount
name: spring-cloud-kubernetes-configuration-watcher
- apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: default
name: namespace-reader
rules:
- apiGroups: ["", "extensions", "apps"]
resources: ["configmaps", "pods", "services", "endpoints", "secrets"]
verbs: ["get", "list", "watch"]
- apiVersion: apps/v1
kind: Deployment
metadata:
name: spring-cloud-kubernetes-configuration-watcher-deployment
spec:
selector:
matchLabels:
app: spring-cloud-kubernetes-configuration-watcher
template:
metadata:
labels:
app: spring-cloud-kubernetes-configuration-watcher
spec:
serviceAccount: spring-cloud-kubernetes-configuration-watcher
containers:
- name: spring-cloud-kubernetes-configuration-watcher
image: springcloud/spring-cloud-kubernetes-configuration-watcher:2.0.1-SNAPSHOT
imagePullPolicy: IfNotPresent
readinessProbe:
httpGet:
port: 8888
path: /actuator/health/readiness
livenessProbe:
httpGet:
port: 8888
path: /actuator/health/liveness
ports:
- containerPort: 8888
The Service Account and associated Role Binding is important for Spring Cloud Kubernetes Configuration to work properly.The controller needs access to read data about ConfigMaps, Pods, Services, Endpoints and Secrets in the Kubernetes cluster.
13.2. Monitoring ConfigMaps and Secrets
Spring Cloud Kubernetes Configuration Watcher will react to changes in ConfigMaps with a label of spring.cloud.kubernetes.config with the value trueor any Secret with a label of spring.cloud.kubernetes.secret with the value true. If the ConfigMap or Secret does not have either of those labelsor the values of those labels is not true then any changes will be ignored.
The labels Spring Cloud Kubernetes Configuration Watcher looks for on ConfigMaps and Secrets can be changed by settingspring.cloud.kubernetes.configuration.watcher.configLabel and spring.cloud.kubernetes.configuration.watcher.secretLabel respectively.
If a change is made to a ConfigMap or Secret with valid labels then Spring Cloud Kubernetes Configuration Watcher will take the name of the ConfigMap or Secretand send a notification to the application with that name.
13.3. HTTP Implementation
The HTTP implementation is what is used by default. When this implementation is used Spring Cloud Kubernetes Configuration Watcher and achange to a ConfigMap or Secret occurs then the HTTP implementation will use the Spring Cloud Kubernetes Discovery Client to fetch allinstances of the application which match the name of the ConfigMap or Secret and send an HTTP POST request to the application’s actuator/refresh endpoint. By default it will send the post request to /actuator/refresh using the port registered in the discovery client.
13.3.1. Non-Default Management Port and Actuator Path
If the application is using a non-default actuator path and/or using a different port for the management endpoints, the Kubernetes service for the applicationcan add an annotation called boot.spring.io/actuator and set its value to the path and port used by the application. For example
apiVersion: v1
kind: Service
metadata:
labels:
app: config-map-demo
name: config-map-demo
annotations:
boot.spring.io/actuator: http://:9090/myactuator/home
spec:
ports:
- name: http
port: 8080
targetPort: 8080
selector:
app: config-map-demo
Another way you can choose to configure the actuator path and/or management port is by settingspring.cloud.kubernetes.configuration.watcher.actuatorPath and spring.cloud.kubernetes.configuration.watcher.actuatorPort.
13.4. Messaging Implementation
The messaging implementation can be enabled by setting profile to either bus-amqp (RabbitMQ) or bus-kafka (Kafka) when the Spring Cloud Kubernetes Configuration Watcherapplication is deployed to Kubernetes.
13.5. Configuring RabbitMQ
When the bus-amqp profile is enabled you will need to configure Spring RabbitMQ to point it to the location of the RabbitMQinstance you would like to use as well as any credentials necessary to authenticate. This can be doneby setting the standard Spring RabbitMQ properties, for example
spring:
rabbitmq:
username: user
password: password
host: rabbitmq
13.6. Configuring Kafka
When the bus-kafka profile is enabled you will need to configure Spring Kafka to point it to the location of the Kafka Brokerinstance you would like to use. This can be done by setting the standard Spring Kafka properties, for example
spring:
kafka:
producer:
bootstrap-servers: localhost:9092
14. Examples
Spring Cloud Kubernetes tries to make it transparent for your applications to consume Kubernetes Native Services byfollowing the Spring Cloud interfaces.
In your applications, you need to add the spring-cloud-kubernetes-discovery dependency to your classpath and remove any other dependency that contains a DiscoveryClient implementation (that is, a Eureka discovery client).The same applies for PropertySourceLocator, where you need to add to the classpath the spring-cloud-kubernetes-config and remove any other dependency that contains a PropertySourceLocator implementation (that is, a configuration server client).
The following projects highlight the usage of these dependencies and demonstrate how you can use these libraries from any Spring Boot application:
Spring Cloud Kubernetes Examples: the ones located inside this repository.
Spring Cloud Kubernetes Full Example: Minions and Boss
Spring Cloud Kubernetes Full Example: SpringOne Platform Tickets Service
Spring Cloud Gateway with Spring Cloud Kubernetes Discovery and Config
Spring Boot Admin with Spring Cloud Kubernetes Discovery and Config
15. Other Resources
This section lists other resources, such as presentations (slides) and videos about Spring Cloud Kubernetes.
Please feel free to submit other resources through pull requests to this repository.
16. Configuration properties
To see the list of all Kubernetes related configuration properties please check the Appendix page.
17. Building
17.1. Basic Compile and Test
To build the source you will need to install JDK 1.8.
Spring Cloud uses Maven for most build-related activities, and youshould be able to get off the ground quite quickly by cloning theproject you are interested in and typing
$ ./mvnw install
|
Note
|
You can also install Maven (>=3.3.3) yourself and run the mvn commandin place of ./mvnw in the examples below. If you do that you alsomight need to add -P spring if your local Maven settings do notcontain repository declarations for spring pre-release artifacts. |
|
Note
|
Be aware that you might need to increase the amount of memoryavailable to Maven by setting a MAVEN_OPTS environment variable witha value like -Xmx512m -XX:MaxPermSize=128m. We try to cover this inthe .mvn configuration, so if you find you have to do it to make abuild succeed, please raise a ticket to get the settings added tosource control. |
The projects that require middleware (i.e. Redis) for testing generallyrequire that a local instance of [Docker](www.docker.com/get-started) is installed and running.
17.2. Documentation
The spring-cloud-build module has a "docs" profile, and if you switchthat on it will try to build asciidoc sources fromsrc/main/asciidoc. As part of that process it will look for aREADME.adoc and process it by loading all the includes, but notparsing or rendering it, just copying it to ${main.basedir}(defaults to ${basedir}, i.e. the root of the project). If there areany changes in the README it will then show up after a Maven build asa modified file in the correct place. Just commit it and push the change.
17.3. Working with the code
If you don’t have an IDE preference we would recommend that you useSpring Tools Suite orEclipse when working with the code. We use them2eclipse eclipse plugin for maven support. Other IDEs and toolsshould also work without issue as long as they use Maven 3.3.3 or better.
17.3.1. Activate the Spring Maven profile
Spring Cloud projects require the 'spring' Maven profile to be activated to resolvethe spring milestone and snapshot repositories. Use your preferred IDE to set thisprofile to be active, or you may experience build errors.
17.3.2. Importing into eclipse with m2eclipse
We recommend the m2eclipse eclipse plugin when working witheclipse. If you don’t already have m2eclipse installed it is available from the "eclipsemarketplace".
|
Note
|
Older versions of m2e do not support Maven 3.3, so once theprojects are imported into Eclipse you will also need to tellm2eclipse to use the right profile for the projects. If yousee many different errors related to the POMs in the projects, checkthat you have an up to date installation. If you can’t upgrade m2e,add the "spring" profile to your settings.xml. Alternatively you cancopy the repository settings from the "spring" profile of the parentpom into your settings.xml. |
17.3.3. Importing into eclipse without m2eclipse
If you prefer not to use m2eclipse you can generate eclipse project metadata using thefollowing command:
$ ./mvnw eclipse:eclipse
The generated eclipse projects can be imported by selecting import existing projectsfrom the file menu.
18. Contributing
Spring Cloud is released under the non-restrictive Apache 2.0 license,and follows a very standard Github development process, using Githubtracker for issues and merging pull requests into master. If you wantto contribute even something trivial please do not hesitate, butfollow the guidelines below.
18.1. Sign the Contributor License Agreement
Before we accept a non-trivial patch or pull request we will need you to sign theContributor License Agreement.Signing the contributor’s agreement does not grant anyone commit rights to the mainrepository, but it does mean that we can accept your contributions, and you will get anauthor credit if we do. Active contributors might be asked to join the core team, andgiven the ability to merge pull requests.
18.2. Code of Conduct
This project adheres to the Contributor Covenant code ofconduct. By participating, you are expected to uphold this code. Please reportunacceptable behavior to spring-code-of-conduct@pivotal.io.
18.3. Code Conventions and Housekeeping
None of these is essential for a pull request, but they will all help. They can also beadded after the original pull request but before a merge.
Use the Spring Framework code format conventions. If you use Eclipseyou can import formatter settings using the
eclipse-code-formatter.xmlfile from theSpringCloud Build project. If using IntelliJ, you can use theEclipse Code FormatterPlugin to import the same file.Make sure all new
.javafiles to have a simple Javadoc class comment with at least an@authortag identifying you, and preferably at least a paragraph on what the class isfor.Add the ASF license header comment to all new
.javafiles (copy from existing filesin the project)Add yourself as an
@authorto the .java files that you modify substantially (morethan cosmetic changes).Add some Javadocs and, if you change the namespace, some XSD doc elements.
A few unit tests would help a lot as well — someone has to do it.
If no-one else is using your branch, please rebase it against the current master (orother target branch in the main project).
When writing a commit message please follow these conventions,if you are fixing an existing issue please add
Fixes gh-XXXXat the end of the commitmessage (where XXXX is the issue number).
18.4. Checkstyle
Spring Cloud Build comes with a set of checkstyle rules. You can find them in the spring-cloud-build-tools module. The most notable files under the module are:
└── src ├── checkstyle │ └── checkstyle-suppressions.xml (3) └── main └── resources ├── checkstyle-header.txt (2) └── checkstyle.xml (1)
Default Checkstyle rules
File header setup
Default suppression rules
18.4.1. Checkstyle configuration
Checkstyle rules are disabled by default. To add checkstyle to your project just define the following properties and plugins.
<properties>
<maven-checkstyle-plugin.failsOnError>true</maven-checkstyle-plugin.failsOnError> (1)
<maven-checkstyle-plugin.failsOnViolation>true
</maven-checkstyle-plugin.failsOnViolation> (2)
<maven-checkstyle-plugin.includeTestSourceDirectory>true
</maven-checkstyle-plugin.includeTestSourceDirectory> (3)
</properties>
<build>
<plugins>
<plugin> (4)
<groupId>io.spring.javaformat</groupId>
<artifactId>spring-javaformat-maven-plugin</artifactId>
</plugin>
<plugin> (5)
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-checkstyle-plugin</artifactId>
</plugin>
</plugins>
<reporting>
<plugins>
<plugin> (5)
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-checkstyle-plugin</artifactId>
</plugin>
</plugins>
</reporting>
</build>
Fails the build upon Checkstyle errors
Fails the build upon Checkstyle violations
Checkstyle analyzes also the test sources
Add the Spring Java Format plugin that will reformat your code to pass most of the Checkstyle formatting rules
Add checkstyle plugin to your build and reporting phases
If you need to suppress some rules (e.g. line length needs to be longer), then it’s enough for you to define a file under ${project.root}/src/checkstyle/checkstyle-suppressions.xml with your suppressions. Example:
<?xml version="1.0"?>
<!DOCTYPE suppressions PUBLIC
"-//Puppy Crawl//DTD Suppressions 1.1//EN"
"https://www.puppycrawl.com/dtds/suppressions_1_1.dtd">
<suppressions>
<suppress files=".*ConfigServerApplication\.java" checks="HideUtilityClassConstructor"/>
<suppress files=".*ConfigClientWatch\.java" checks="LineLengthCheck"/>
</suppressions>
It’s advisable to copy the ${spring-cloud-build.rootFolder}/.editorconfig and ${spring-cloud-build.rootFolder}/.springformat to your project. That way, some default formatting rules will be applied. You can do so by running this script:
$ curl https://raw.githubusercontent.com/spring-cloud/spring-cloud-build/master/.editorconfig -o .editorconfig
$ touch .springformat
18.5. IDE setup
18.5.1. Intellij IDEA
In order to setup Intellij you should import our coding conventions, inspection profiles and set up the checkstyle plugin.The following files can be found in the Spring Cloud Build project.
└── src ├── checkstyle │ └── checkstyle-suppressions.xml (3) └── main └── resources ├── checkstyle-header.txt (2) ├── checkstyle.xml (1) └── intellij ├── Intellij_Project_Defaults.xml (4) └── Intellij_Spring_Boot_Java_Conventions.xml (5)
Default Checkstyle rules
File header setup
Default suppression rules
Project defaults for Intellij that apply most of Checkstyle rules
Project style conventions for Intellij that apply most of Checkstyle rules
Go to File → Settings → Editor → Code style. There click on the icon next to the Scheme section. There, click on the Import Scheme value and pick the Intellij IDEA code style XML option. Import the spring-cloud-build-tools/src/main/resources/intellij/Intellij_Spring_Boot_Java_Conventions.xml file.
Go to File → Settings → Editor → Inspections. There click on the icon next to the Profile section. There, click on the Import Profile and import the spring-cloud-build-tools/src/main/resources/intellij/Intellij_Project_Defaults.xml file.
To have Intellij work with Checkstyle, you have to install the Checkstyle plugin. It’s advisable to also install the Assertions2Assertj to automatically convert the JUnit assertions
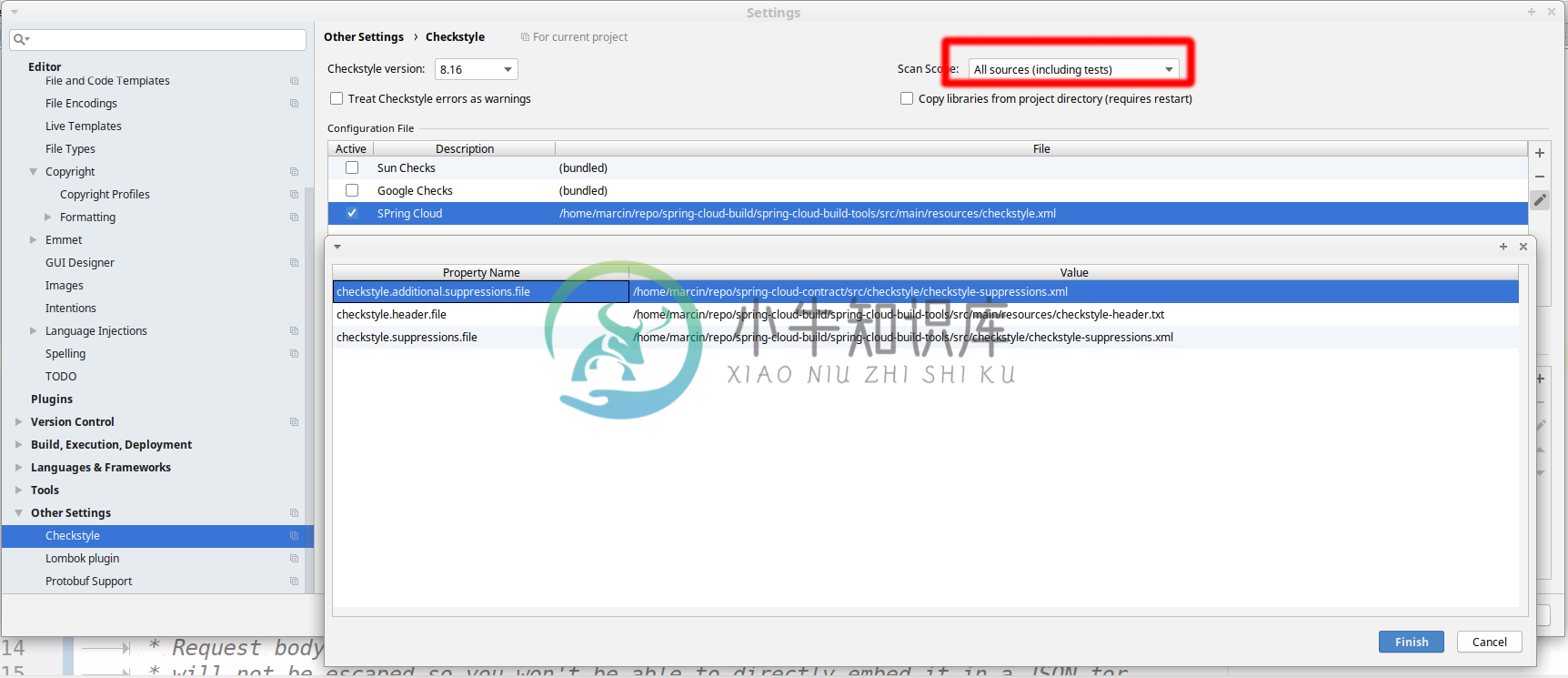
Go to File → Settings → Other settings → Checkstyle. There click on the + icon in the Configuration file section. There, you’ll have to define where the checkstyle rules should be picked from. In the image above, we’ve picked the rules from the cloned Spring Cloud Build repository. However, you can point to the Spring Cloud Build’s GitHub repository (e.g. for the checkstyle.xml : raw.githubusercontent.com/spring-cloud/spring-cloud-build/master/spring-cloud-build-tools/src/main/resources/checkstyle.xml). We need to provide the following variables:
checkstyle.header.file- please point it to the Spring Cloud Build’s,spring-cloud-build-tools/src/main/resources/checkstyle-header.txtfile either in your cloned repo or via theraw.githubusercontent.com/spring-cloud/spring-cloud-build/master/spring-cloud-build-tools/src/main/resources/checkstyle-header.txtURL.checkstyle.suppressions.file- default suppressions. Please point it to the Spring Cloud Build’s,spring-cloud-build-tools/src/checkstyle/checkstyle-suppressions.xmlfile either in your cloned repo or via theraw.githubusercontent.com/spring-cloud/spring-cloud-build/master/spring-cloud-build-tools/src/checkstyle/checkstyle-suppressions.xmlURL.checkstyle.additional.suppressions.file- this variable corresponds to suppressions in your local project. E.g. you’re working onspring-cloud-contract. Then point to theproject-root/src/checkstyle/checkstyle-suppressions.xmlfolder. Example forspring-cloud-contractwould be:/home/username/spring-cloud-contract/src/checkstyle/checkstyle-suppressions.xml.
|
Important
|
Remember to set the Scan Scope to All sources since we apply checkstyle rules for production and test sources. |
-
k8s集群apiserver访问方式 1、通过证书认证 2、通过token认证 本地开发spring-cloud-k8s时使用token访问apiserver 1、获取token kubectl get secret kubectl get secret -n kube-system |grep cluster |awk '{print $1}' -n kube-system -o json |
-
第一次尝试.minikube v1.7.3 和 spring-cloud-kubernetes 1.0.x 永远不会刷新configmap ,原因是 注入进environment的propertySource是BootstrapPropertySource类型,既不是CompositePropertySource的实例,也不是ConfigMapPropertySource的实例 第二次尝试.mi
-
我们最近从Spring Cloud Netflix Ribbon迁移到Spring Cloud LoadBalancer,并使用Spring Cloud kubernetes作为发现客户端。 现在spring.cloud.kubernetes.ribbon.mode(https://cloud.spring.io/spring-cloud-static/spring-cloud-kubernete
-
Spring Cloud为开发人员提供了快速构建分布式系统中一些常见模式的工具(例如配置管理,服务发现,断路器,智能路由,微代理,控制总线)。分布式系统的协调导致了样板模式, 使用Spring Cloud开发人员可以快速地支持实现这些模式的服务和应用程序。他们将在任何分布式环境中运行良好,包括开发人员自己的笔记本电脑,裸机数据中心,以及Cloud Foundry等托管平台。
-
Spring Cloud 为开发人员提供了工具,以快速构建分布式系统中的某些常见模式(例如:配置管理、服务发现、智能路由、微代理、控制总线、一次性令牌、全局锁、分布式会话、群集状态等)。分布式系统的协调导致了样板式样,并且使用Spring Cloud开发人员可以快速站起来实现这些样板的服务和应用程序。它们可以在任何分布式环境中正常工作,包括开发人员自己的笔记本电脑,裸机数据中心以及Cloud Fo
-
Cloudfoundry的Spring Cloud可以轻松地在Cloud Foundry(平台即服务)中运行 Spring Cloud应用程序 。Cloud Foundry有一个“服务”的概念,它是“绑定”到应用程序的中间件,本质上为其提供包含凭据的环境变量(例如,用于服务的位置和用户名)。 spring-cloud-cloudfoundry-web项目为Cloud Foundry中的webapp
-
主要内容:Spring Cloud Config,Spring Cloud Config 工作原理,Spring Cloud Config 的特点,搭建 Config 服务端,搭建 Config 客户端,手动刷新配置,Config+Bus 实现配置的动态刷新在分布式微服务系统中,几乎所有服务的运行都离不开配置文件的支持,这些配置文件通常由各个服务自行管理,以 properties 或 yml 格式保存在各个微服务的类路径下,例如 application.properties 或 applicat
-
主要内容:API 网关,Spring Cloud Gateway ,Gateway 的工作流程,Predicate 断言,Spring Cloud Gateway 动态路由,Filter 过滤器在微服务架构中,一个系统往往由多个微服务组成,而这些服务可能部署在不同机房、不同地区、不同域名下。这种情况下,客户端(例如浏览器、手机、软件工具等)想要直接请求这些服务,就需要知道它们具体的地址信息,例如 IP 地址、端口号等。 这种客户端直接请求服务的方式存在以下问题: 当服务数量众多时,客户端需要维护