API创新不会触发AWS API网关基于自定义请求的lambda授权程序
为我的AWS API网关创建了一个简单的基于请求的基本授权程序(https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-use-lambda-authorizer.html)
当测试授权程序时(使用虚拟设置,验证授权头是否有键“测试”),授权程序工作正常,但是当直接从endpoint调用API时,授权程序根本没有被调用,我得到了我的API响应(应该被阻止因为没有传递标头)。
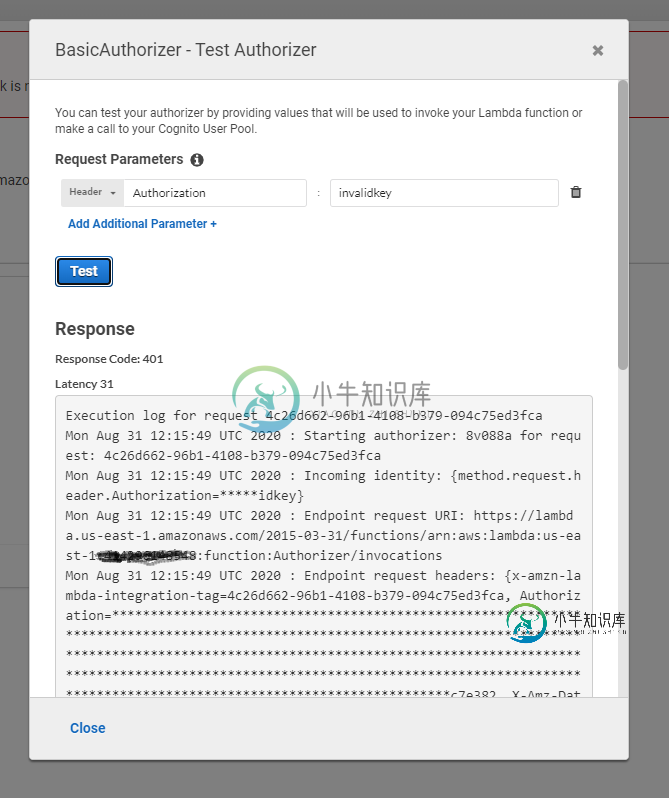
具有无效密钥的授权人测试:正在获取预期值
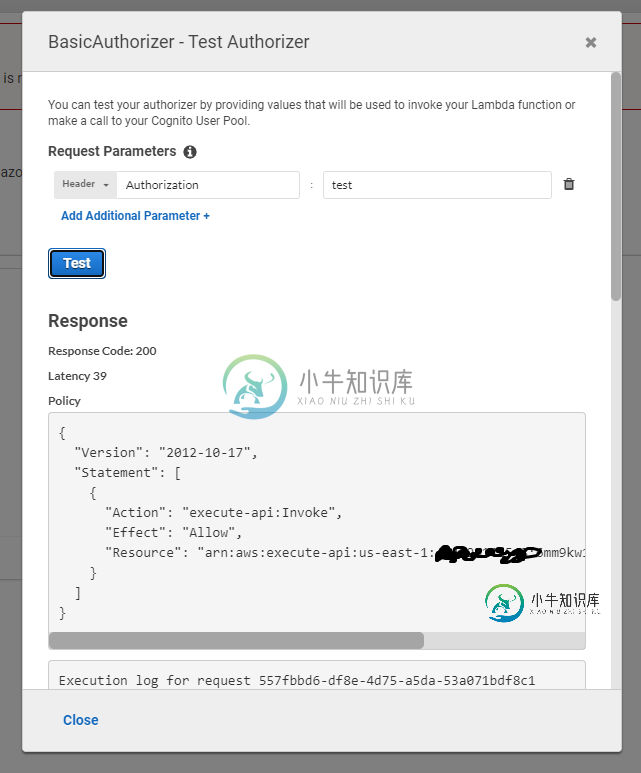
使用有效密钥进行授权程序测试:获得预期200
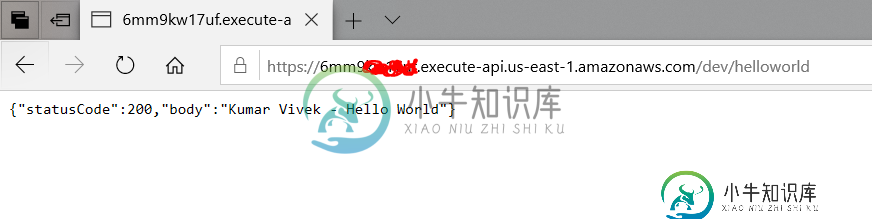
从web直接调用APIendpoint成功:
API网关的我的资源策略仅限于特定IP范围:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:us-east-1:111111111111:6mm9kw17uf/*/*/*"
},
{
"Effect": "Deny",
"Principal": "*",
"Action": "execute-api:Invoke",
"Resource": "arn:aws:execute-api:us-east-1:111111111111:6mm9kw17uf/*/*/*",
"Condition": {
"NotIpAddress": {
"aws:SourceIp": "XXXXXXX"
}
}
}
]
}
授权方Lambda代码:
exports.handler = function(event, context, callback) {
console.log('Received event:', JSON.stringify(event, null, 2));
// Retrieve request parameters from the Lambda function input:
var headers = event.headers;
// Parse the input for the parameter values
var tmp = event.methodArn.split(':');
var apiGatewayArnTmp = tmp[5].split('/');
var awsAccountId = tmp[4];
var region = tmp[3];
var restApiId = apiGatewayArnTmp[0];
var stage = apiGatewayArnTmp[1];
var method = apiGatewayArnTmp[2];
var resource = '/'; // root resource
if (apiGatewayArnTmp[3]) {
resource += apiGatewayArnTmp[3];
}
// Perform authorization to return the Allow policy for correct parameters and
// the 'Unauthorized' error, otherwise.
var authResponse = {};
var condition = {};
condition.IpAddress = {};
if (headers.Authorization === "test") {
callback(null, generateAllow('me', event.methodArn));
} else {
callback("Unauthorized");
}
}
// Help function to generate an IAM policy
var generatePolicy = function(principalId, effect, resource) {
// Required output:
var authResponse = {};
authResponse.principalId = principalId;
if (effect && resource) {
var policyDocument = {};
policyDocument.Version = '2012-10-17';
policyDocument.Statement = [];
var statementOne = {};
statementOne.Action = 'execute-api:Invoke';
statementOne.Effect = effect;
statementOne.Resource = resource;
policyDocument.Statement[0] = statementOne;
authResponse.policyDocument = policyDocument;
}
return authResponse;
}
var generateAllow = function(principalId, resource) {
return generatePolicy(principalId, 'Allow', resource);
}
var generateDeny = function(principalId, resource) {
return generatePolicy(principalId, 'Deny', resource);
}
我已经尝试过的:
- 添加授权人后,我已经重新部署了API。
共有1个答案
我尝试使用我自己的API网关复制这个问题,但我还没有发现lambda函数有任何问题。它按预期工作。
授权呼叫示例:
curl -i -w "\n" --http1.1 -H 'Authorization: test' https://xxxxx.execute-api.us-east-1.amazonaws.com/dev/helloworld
HTTP/1.1 200 OK
Date: Sun, 06 Sep 2020 11:22:30 GMT
Content-Type: application/json
Content-Length: 67
Connection: keep-alive
x-amzn-RequestId: 4213f276-737c-4481-bbac-3c4ecd767b6f
x-amz-apigw-id: ScPyeFInoAMFYKg=
X-Amzn-Trace-Id: Root=1-5f54c676-9e0c8bbe6093d8889f6b2035;Sampled=0
{
"statusCode": 200,
"message": "Hello from API Gateway!"
}
非授权呼叫示例:
curl -i -w "\n" --http1.1 -H 'Authorization: invalid' https://xxxx.execute-api.us-east-1.amazonaws.com/dev/helloworld
HTTP/1.1 401 Unauthorized
Date: Sun, 06 Sep 2020 11:25:36 GMT
Content-Type: application/json
Content-Length: 26
Connection: keep-alive
x-amzn-RequestId: 42a1d47c-aab5-4b72-b8eb-469fed383b26
x-amzn-ErrorType: UnauthorizedException
x-amz-apigw-id: ScQPpFUwoAMFRdA=
{"message":"Unauthorized"}
未提供标题值的示例:
curl -i -w "\n" --http1.1 https://xxxx.execute-api.us-east-1.amazonaws.com/dev/helloworld
HTTP/1.1 401 Unauthorized
Date: Sun, 06 Sep 2020 11:26:15 GMT
Content-Type: application/json
Content-Length: 26
Connection: keep-alive
x-amzn-RequestId: 982944f2-ac1d-4eee-8776-7bfa76314d2b
x-amzn-ErrorType: UnauthorizedException
x-amz-apigw-id: ScQVwGmpoAMFfSA=
{"message":"Unauthorized"}
不过要考虑的事情:
- 当您将授权程序添加到api方法时,您必须再次部署阶段。
- 直到新的授权程序开始工作需要时间。因此,在您启用它并创建新阶段后,必须等待几分钟,直到它开始工作
-
但是看起来在我的lambda响应和API网关之间发生了一些奇怪的事情, 变量在内部的某个地方被压缩得更低, 而我仍然得到了相同的解析错误, 它会接受其他格式的响应吗?字符串也不起作用。 我还应该尝试什么?我的策略格式错误吗? 我从这些站点获得了两种不同的策略格式- 1。http://docs.aws.amazon.com/apigateway/latest/developerguide/use-c
-
我是API网关的新手。我尝试使用“自定义授权程序”。我遵循了下面的文档,并使用了网站提供的示例代码。https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-use-lambda-authorizer.html “令牌类型的lambda授权者”是工作的。 但是... 我对“请求类型”感到困惑,不知道如何将quer
-
我正在AWS lambda上使用无服务器框架构建一个REST服务。我已经创建了一个自定义授权器,在调用lambdas时调用它。当我运行无服务器脱机时,一切正常。当我部署时,我在AP网关中得到一个错误。我已经在API网关中启用了日志,但没有任何东西写入日志。 下面是我的Serverless.yml文件: 我的授权处理程序如下所示。该方法获取我的身份验证令牌并使用JOSE验证它,并为用户和一些角色返回
-
Mono Apr 10 09:42:35 UTC 2017:转换后的endpoint请求主体:{“Type”:“Token”,“AuthorizationToken”:“ABC123”,“MethodArn”:“arn:aws:execute-api:ap-southeast-1:007183653813:OHLQXU9P57/null/Get/”}Mono Apr 10 09:42:36 UTC
-
如何从API网关中的自定义授权器lambda函数获取日志记录?我不想为API启用日志记录。我需要从授权器lambda函数日志记录。我使用了一个python lambda函数,并且在代码中有打印。我想查看云观察日志中的指纹。但在云观察中看不到原木。我也没有错误。我缺少什么? Lambda有execution role role/service-role/mylambdarole。此角色具有写入clo

