在Spring Boot应用程序中为AWS Beanstalk的nginx设置HTTP到HTTPS重定向
我有一个Spring Boot应用程序在Beanstek上运行,我最近想让我的整个网站由HTTPS保护,所以我想默认情况下将所有HTTP流量重定向到HTTPS。
我已经用Amazon Certificate Manager安装了SSL证书,它被我的Amazon ELB负载平衡器使用,所以HTTPS将在那里终止。
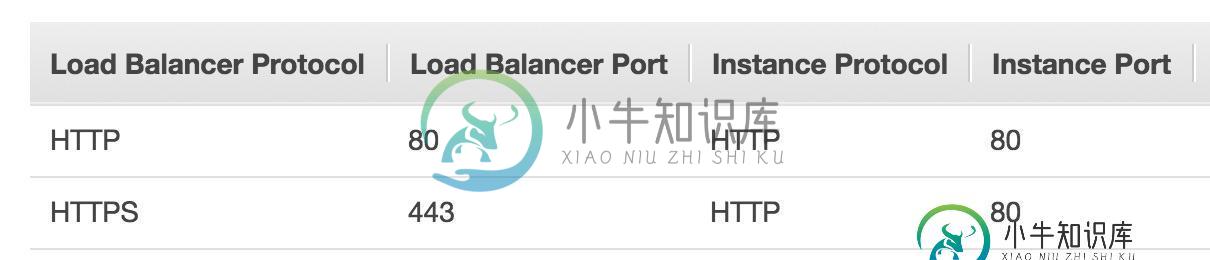
我还注意到,默认情况下,负载均衡器上也有一个监听端口80(实例端口),然后最后将其转发到我的Spring Boot应用程序的nginx。
因此,我试图通过将此conf文件放在. ebextsion/nginx/conf. d/elasticbeanstek/00_nginx_https_rw.conf来进行重定向,而. ebextsion文件夹位于我的Spring Boot回购中的src/main/资源下:
files:
"/tmp/45_nginx_https_rw.sh":
owner: root
group: root
mode: "000644"
content: |
#! /bin/bash
CONFIGURED=`grep -c "return 301 https" /opt/elasticbeanstalk/support/conf/webapp_healthd.conf`
if [ $CONFIGURED = 0 ]
then
sed -i '/listen 80;/a \ if ($http_x_forwarded_proto = "http") { return 301 https://$host$request_uri; }\n' /opt/elasticbeanstalk/support/conf/webapp_healthd.conf
logger -t nginx_rw "https rewrite rules added"
exit 0
else
logger -t nginx_rw "https rewrite rules already set"
exit 0
fi
container_commands:
00_appdeploy_rewrite_hook:
command: cp -v /tmp/45_nginx_https_rw.sh /opt/elasticbeanstalk/hooks/appdeploy/enact
01_configdeploy_rewrite_hook:
command: cp -v /tmp/45_nginx_https_rw.sh /opt/elasticbeanstalk/hooks/configdeploy/enact
02_rewrite_hook_perms:
command: chmod 755 /opt/elasticbeanstalk/hooks/appdeploy/enact/45_nginx_https_rw.sh /opt/elasticbeanstalk/hooks/configdeploy/enact/45_nginx_https_rw.sh
03_rewrite_hook_ownership:
command: chown root:users /opt/elasticbeanstalk/hooks/appdeploy/enact/45_nginx_https_rw.sh /opt/elasticbeanstalk/hooks/configdeploy/enact/45_nginx_https_rw.sh
04_reload_nginx:
command: "sudo service nginx reload"
我用这个conf文件部署了我的Spring Boot应用程序,并在Beanstalk中执行了“重启应用程序服务器”,但它仍然不会从HTTP重定向到HTTPS
我也在conf文件中尝试了这个方法,但它也不起作用:
listen 80;
# ELB stores the protocol used between the client
# and the load balancer in the X-Forwarded-Proto request header.
# Check for 'https' and redirect if not
if ($http_x_forwarded_proto != 'https') {
rewrite ^ https://$host$request_uri? permanent;
}
server_name mothersquad.com www.mothersquad.com
这是我的Nginx访问权限。尝试转到网站的HTTP版本时记录:
172.31.42.155 - - [28/Sep/2017:07:38:53 +0000] "GET /health_check HTTP/1.1" 200 2 "-" "ELB-HealthChecker/1.0" "-"
172.31.42.155 - - [28/Sep/2017:07:39:03 +0000] "GET /health_check HTTP/1.1" 200 2 "-" "ELB-HealthChecker/1.0" "-"
172.31.42.155 - - [28/Sep/2017:07:39:13 +0000] "GET /health_check HTTP/1.1" 200 2 "-" "ELB-HealthChecker/1.0" "-"
172.31.42.155 - - [28/Sep/2017:07:39:23 +0000] "GET /health_check HTTP/1.1" 200 2 "-" "ELB-HealthChecker/1.0" "-"
172.31.42.155 - - [28/Sep/2017:07:39:23 +0000] "GET / HTTP/1.1" 200 93279 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:23 +0000] "GET /css/landing.css HTTP/1.1" 200 13132 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:23 +0000] "GET /css/landing_bootstrap.css HTTP/1.1" 200 134640 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:23 +0000] "GET /js/landing.js HTTP/1.1" 200 5627 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/logo.png HTTP/1.1" 200 6830 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/tracery.png HTTP/1.1" 200 23045 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-4.jpg HTTP/1.1" 200 17441 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-1.jpg HTTP/1.1" 200 24258 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-2.jpg HTTP/1.1" 200 20504 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-5.jpg HTTP/1.1" 200 18711 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-3.jpg HTTP/1.1" 200 20686 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/virtualgroup.jpg HTTP/1.1" 200 46406 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-6.jpg HTTP/1.1" 200 21364 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/squad-photo-7.jpg HTTP/1.1" 200 18472 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/tracery-red.png HTTP/1.1" 200 2500 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/bg1.jpg HTTP/1.1" 200 48181 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
172.31.42.155 - - [28/Sep/2017:07:39:24 +0000] "GET /images/landing/bg2.jpg HTTP/1.1" 200 116554 "http://www.example.com/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.79 Safari/537.36" "172.113.254.101"
我没有在错误中看到任何错误。日志
我还错过了什么?谢谢
共有1个答案
如果您已经在负载平衡器上安装了证书,我建议在LB处终止SSL(假设您的VPC是安全的)。尝试设置参数server。在应用程序属性中使用前向标题,将其设置为true。这将使你的启动应用程序尊重X-Forwarded-Proto和X-Forward-For-For头文件。
完成后,移除LB上的端口80侦听器,这样应用程序只能通过443访问。
-
我在关注堆栈问题如何设置lets加密SSL证书并在Spring Boot应用程序中使用它?将我的Springboot应用程序配置为使用https(certbot),但我的Nginx没有正确重定向到我的应用程序。 更多内容:我正在使用Cloudflare重定向www.example。com(我的域)向我拥有Nginx和Springboot应用程序的计算机发出请求。我希望Nginx将端口80上的htt
-
我有一个域有3个子域: 在我的nginx上有以下3个配置: API null
-
我有一个使用http和https的SpringBoot 2.0应用程序。因此,在端口9080上,它服务于http协议,在端口9443上,它工作正常。我唯一想要的是重定向,如果用户输入例如:http://localhost:9443/e1 综上所述: http://localhost:9080/e1 https://localhost:9443/e1 http://localhost:9443/e1
-
我想问一下HTTP到HTTPS的重定向。正如我们所知,重定向是通过从web服务器端重定向来实现的。但是,当涉及到https重定向时,它可以通过两种方式完成,服务器端()和应用程序端()。我想知道: 以下哪种方法有效且性能更好。 考虑到同一服务器上的多个域和域,每种方法的优缺点 非常感谢。 参考: 将Laravel中的WWW重定向到非WWW-堆栈溢出
-
我正在构建一个Rails 4应用程序,其中包含前端网站和公开的API。该API用作移动应用程序和桌面应用程序的后端。 我在Heroku上部署了这个应用程序。因为网站有一个订购系统,我决定强制ssl全球。当我发出HTTP请求时,站点成功地将我重定向到HTTPS。 但是,当我使用命令行中的cURL向我公开的API发出HTTP请求时,我没有得到预期的响应。相反,我在我的Heroku日志中看到了一条301
-
我想启用或禁用具有外部配置的SSL/TLS,这些配置可以在应用程序启动期间提供。应用程序应该支持http和HTTPS的所有crud操作。 既然上面的属性是不推荐使用的,那么我如何在不使用配置文件的情况下实现它。

