OpenShift/键盘斗篷4.8.3。登录到管理控制台无限重定向循环
我已经使用了一段时间,从每1k展现的收入安装没有任何问题,到目前为止。现在,我们正在迁移我们的大部分服务到OpenShift集群(3.9)。在迁移到我当前服务器的最新版本之前(4.8.3),我正在OpenShift集群中进行一个干净的安装,问题来了。
我在我的Openshift集群中使用官方镜像jboss/keycloak:late,并且POD已经启动并运行。但是每次我尝试访问 securtiy-admin-console 时,无论我使用什么浏览器,成功登录后它都会进入无限循环。
到目前为止,这就是我得到的:-访问安全管理控制台https://keycloak.openshift.cluster/auth/admin/master/console/#/进入重定向循环。
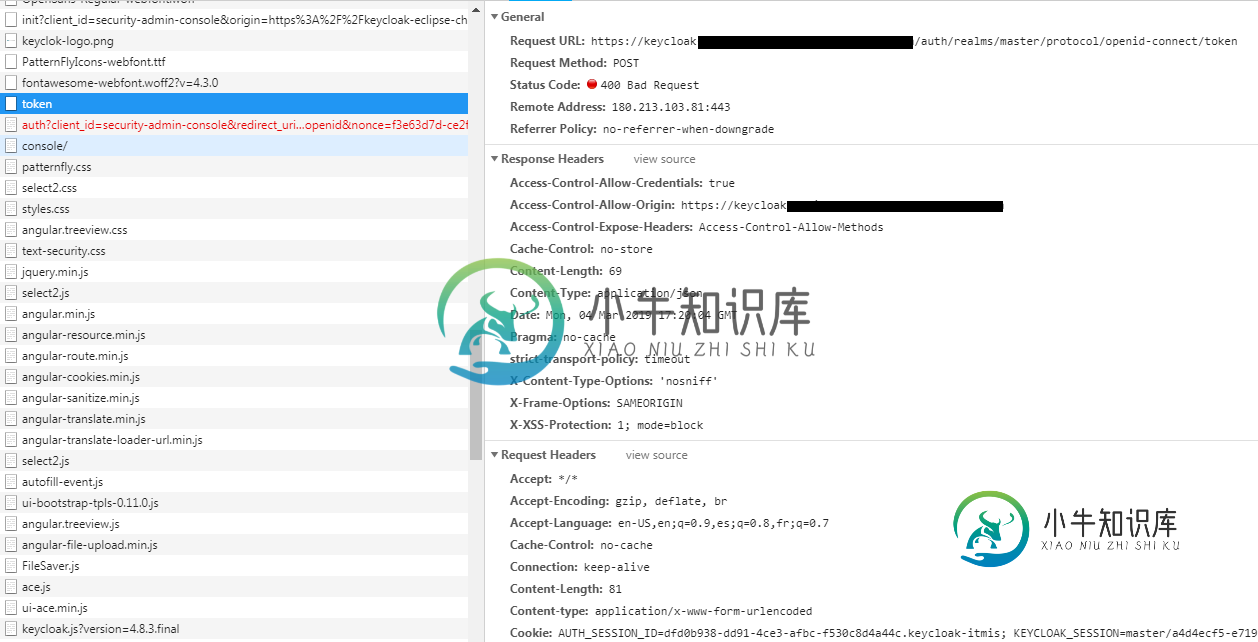
之后,我在日志中看到了这个错误:
17:20:06,765 DEBUG [org.keycloak.authentication.AuthenticationProcessor] (default task-8) AUTHENTICATE CLIENT
17:20:06,765 DEBUG [org.keycloak.authentication.ClientAuthenticationFlow] (default task-8) client authenticator: client-secret
17:20:06,765 DEBUG [org.keycloak.authentication.ClientAuthenticationFlow] (default task-8) client authenticator SUCCESS: client-secret
17:20:06,765 DEBUG [org.keycloak.authentication.ClientAuthenticationFlow] (default task-8) Client security-admin-console authenticated by client-secret
17:20:06,765 DEBUG [org.keycloak.jose.jws.DefaultTokenManager] (default task-8) Failed to decode token: org.keycloak.jose.jws.JWSInputException: java.lang.IllegalArgumentException: Parsing error
at org.keycloak.jose.jws.JWSInput.<init>(JWSInput.java:58)
at org.keycloak.jose.jws.DefaultTokenManager.decode(DefaultTokenManager.java:63)
at org.keycloak.protocol.oidc.TokenManager.toRefreshToken(TokenManager.java:370)
at org.keycloak.protocol.oidc.TokenManager.verifyRefreshToken(TokenManager.java:336)
at org.keycloak.protocol.oidc.TokenManager.refreshAccessToken(TokenManager.java:254)
at org.keycloak.protocol.oidc.endpoints.TokenEndpoint.refreshTokenGrant(TokenEndpoint.java:462)
at org.keycloak.protocol.oidc.endpoints.TokenEndpoint.processGrantRequest(TokenEndpoint.java:185)
at sun.reflect.GeneratedMethodAccessor499.invoke(Unknown Source)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:498)
at org.jboss.resteasy.core.MethodInjectorImpl.invoke(MethodInjectorImpl.java:140)
at org.jboss.resteasy.core.ResourceMethodInvoker.internalInvokeOnTarget(ResourceMethodInvoker.java:509)
at org.jboss.resteasy.core.ResourceMethodInvoker.invokeOnTargetAfterFilter(ResourceMethodInvoker.java:399)
at org.jboss.resteasy.core.ResourceMethodInvoker.lambda$invokeOnTarget$0(ResourceMethodInvoker.java:363)
at org.jboss.resteasy.core.interception.PreMatchContainerRequestContext.filter(PreMatchContainerRequestContext.java:358)
at org.jboss.resteasy.core.ResourceMethodInvoker.invokeOnTarget(ResourceMethodInvoker.java:365)
at org.jboss.resteasy.core.ResourceMethodInvoker.invoke(ResourceMethodInvoker.java:337)
at org.jboss.resteasy.core.ResourceLocatorInvoker.invokeOnTargetObject(ResourceLocatorInvoker.java:137)
at org.jboss.resteasy.core.ResourceLocatorInvoker.invoke(ResourceLocatorInvoker.java:106)
at org.jboss.resteasy.core.ResourceLocatorInvoker.invokeOnTargetObject(ResourceLocatorInvoker.java:132)
at org.jboss.resteasy.core.ResourceLocatorInvoker.invoke(ResourceLocatorInvoker.java:100)
at org.jboss.resteasy.core.SynchronousDispatcher.invoke(SynchronousDispatcher.java:443)
at org.jboss.resteasy.core.SynchronousDispatcher.lambda$invoke$4(SynchronousDispatcher.java:233)
at org.jboss.resteasy.core.SynchronousDispatcher.lambda$preprocess$0(SynchronousDispatcher.java:139)
at org.jboss.resteasy.core.interception.PreMatchContainerRequestContext.filter(PreMatchContainerRequestContext.java:358)
at org.jboss.resteasy.core.SynchronousDispatcher.preprocess(SynchronousDispatcher.java:142)
at org.jboss.resteasy.core.SynchronousDispatcher.invoke(SynchronousDispatcher.java:219)
at org.jboss.resteasy.plugins.server.servlet.ServletContainerDispatcher.service(ServletContainerDispatcher.java:227)
at org.jboss.resteasy.plugins.server.servlet.HttpServletDispatcher.service(HttpServletDispatcher.java:56)
at org.jboss.resteasy.plugins.server.servlet.HttpServletDispatcher.service(HttpServletDispatcher.java:51)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:791)
at io.undertow.servlet.handlers.ServletHandler.handleRequest(ServletHandler.java:74)
at io.undertow.servlet.handlers.FilterHandler$FilterChainImpl.doFilter(FilterHandler.java:129)
at org.keycloak.services.filters.KeycloakSessionServletFilter.doFilter(KeycloakSessionServletFilter.java:90)
at io.undertow.servlet.core.ManagedFilter.doFilter(ManagedFilter.java:61)
at io.undertow.servlet.handlers.FilterHandler$FilterChainImpl.doFilter(FilterHandler.java:131)
at io.undertow.servlet.handlers.FilterHandler.handleRequest(FilterHandler.java:84)
at io.undertow.servlet.handlers.security.ServletSecurityRoleHandler.handleRequest(ServletSecurityRoleHandler.java:62)
at io.undertow.servlet.handlers.ServletChain$1.handleRequest(ServletChain.java:68)
at io.undertow.servlet.handlers.ServletDispatchingHandler.handleRequest(ServletDispatchingHandler.java:36)
at org.wildfly.extension.undertow.security.SecurityContextAssociationHandler.handleRequest(SecurityContextAssociationHandler.java:78)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.servlet.handlers.security.SSLInformationAssociationHandler.handleRequest(SSLInformationAssociationHandler.java:132)
at io.undertow.servlet.handlers.security.ServletAuthenticationCallHandler.handleRequest(ServletAuthenticationCallHandler.java:57)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.security.handlers.AbstractConfidentialityHandler.handleRequest(AbstractConfidentialityHandler.java:46)
at io.undertow.servlet.handlers.security.ServletConfidentialityConstraintHandler.handleRequest(ServletConfidentialityConstraintHandler.java:64)
at io.undertow.security.handlers.AuthenticationMechanismsHandler.handleRequest(AuthenticationMechanismsHandler.java:60)
at io.undertow.servlet.handlers.security.CachedAuthenticatedSessionHandler.handleRequest(CachedAuthenticatedSessionHandler.java:77)
at io.undertow.security.handlers.NotificationReceiverHandler.handleRequest(NotificationReceiverHandler.java:50)
at io.undertow.security.handlers.AbstractSecurityContextAssociationHandler.handleRequest(AbstractSecurityContextAssociationHandler.java:43)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at org.wildfly.extension.undertow.security.jacc.JACCContextIdHandler.handleRequest(JACCContextIdHandler.java:61)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at org.wildfly.extension.undertow.deployment.GlobalRequestControllerHandler.handleRequest(GlobalRequestControllerHandler.java:68)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.servlet.handlers.ServletInitialHandler.handleFirstRequest(ServletInitialHandler.java:292)
at io.undertow.servlet.handlers.ServletInitialHandler.access$100(ServletInitialHandler.java:81)
at io.undertow.servlet.handlers.ServletInitialHandler$2.call(ServletInitialHandler.java:138)
at io.undertow.servlet.handlers.ServletInitialHandler$2.call(ServletInitialHandler.java:135)
at io.undertow.servlet.core.ServletRequestContextThreadSetupAction$1.call(ServletRequestContextThreadSetupAction.java:48)
at io.undertow.servlet.core.ContextClassLoaderSetupAction$1.call(ContextClassLoaderSetupAction.java:43)
at org.wildfly.extension.undertow.security.SecurityContextThreadSetupAction.lambda$create$0(SecurityContextThreadSetupAction.java:105)
at org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction.lambda$create$0(UndertowDeploymentInfoService.java:1502)
at org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction.lambda$create$0(UndertowDeploymentInfoService.java:1502)
at org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction.lambda$create$0(UndertowDeploymentInfoService.java:1502)
at org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction.lambda$create$0(UndertowDeploymentInfoService.java:1502)
at io.undertow.servlet.handlers.ServletInitialHandler.dispatchRequest(ServletInitialHandler.java:272)
at io.undertow.servlet.handlers.ServletInitialHandler.access$000(ServletInitialHandler.java:81)
at io.undertow.servlet.handlers.ServletInitialHandler$1.handleRequest(ServletInitialHandler.java:104)
at io.undertow.server.Connectors.executeRootHandler(Connectors.java:360)
at io.undertow.server.HttpServerExchange$1.run(HttpServerExchange.java:830)
at org.jboss.threads.ContextClassLoaderSavingRunnable.run(ContextClassLoaderSavingRunnable.java:35)
at org.jboss.threads.EnhancedQueueExecutor.safeRun(EnhancedQueueExecutor.java:1985)
at org.jboss.threads.EnhancedQueueExecutor$ThreadBody.doRunTask(EnhancedQueueExecutor.java:1487)
at org.jboss.threads.EnhancedQueueExecutor$ThreadBody.run(EnhancedQueueExecutor.java:1378)
at java.lang.Thread.run(Thread.java:748)
Caused by: java.lang.IllegalArgumentException: Parsing error
at org.keycloak.jose.jws.JWSInput.<init>(JWSInput.java:45)
... 76 more
17:20:06,766 WARN [org.keycloak.events] (default task-8) type=REFRESH_TOKEN_ERROR, realmId=master, clientId=security-admin-console, userId=null, ipAddress=XXX.XXX.XXX.XXX, error=invalid_token, grant_type=refresh_token, client_auth_method=client-secret
17:20:06,766 DEBUG [org.keycloak.services.resources.Cors] (default task-8) Added CORS headers to response
17:20:06,766 DEBUG [org.keycloak.services.resources.Cors] (default task-8) Added CORS headers to response
17:20:06,766 DEBUG [org.keycloak.services.resources.Cors] (default task-8) Added CORS headers to response
>
我创建了多个用户,并且始终具有相同的行为。
从 ADMIN-CLI 一切正常,我可以登录并执行 admin-cli 允许的任何操作。
在我们的网络中,任何没有TLS/SSL的流量都被默认阻止,因此我们使用配置为边缘的路由器并重定向非安全流量。
关于部署/POD配置,按照docker容器的说明,我将以下环境变量添加到KeyCloak部署中:
- PROXY_ADDRESS_FORWARDING=真
- KEYCLOAK_USER=管理员
- KEYCLOAK_PASSWORD=******
- DB_ADDR=postgres.openshift。群集
- DB_PORT=5432
- DB_DATABASE=密钥斗篷
- DB_USER=密钥斗篷
- DB_PASSWORD=******
- KEYCLOAK_HOSTNAME=密钥斗篷
我检查了一下,Openshift路由器默认添加了正确的标头,它们是:
- X-转发-主机
- X-转发-原型
- X-转发-端口
以下是KeyCloak POD的路由器配置:
mode http
option redispatch
option forwardfor
balance leastconn
timeout check 5000ms
http-request set-header X-Forwarded-Host %[req.hdr(host)]
http-request set-header X-Forwarded-Port %[dst_port]
http-request set-header X-Forwarded-Proto http if !{ ssl_fc }
http-request set-header X-Forwarded-Proto https if { ssl_fc }
http-request set-header Forwarded for=%[src];host=%[req.hdr(host)];proto=%[req.hdr(X-Forwarded-Proto)]
cookie *************************** insert indirect nocache httponly secure
server pod:keycloak-50-k75pr:keycloak:XXX.XXX.XXX.XXX:8080 XXX.XXX.XXX.XXX:8080 cookie ***************************** weight 256 check inter 5000ms
我正在做的唯一修改是将我的OpenShift集群的CA证书添加到容器的cacert中。
我的主领域配置是默认配置,但内容如下:
[ {
"id" : "master",
"realm" : "master",
"displayName" : "Keycloak",
"displayNameHtml" : "<div class=\"kc-logo-text\"><span>Keycloak</span></div>",
"notBefore" : 0,
"revokeRefreshToken" : false,
"refreshTokenMaxReuse" : 0,
"accessTokenLifespan" : 60,
"accessTokenLifespanForImplicitFlow" : 900,
"ssoSessionIdleTimeout" : 1800,
"ssoSessionMaxLifespan" : 36000,
"ssoSessionIdleTimeoutRememberMe" : 0,
"ssoSessionMaxLifespanRememberMe" : 0,
"offlineSessionIdleTimeout" : 2592000,
"offlineSessionMaxLifespanEnabled" : false,
"offlineSessionMaxLifespan" : 5184000,
"accessCodeLifespan" : 60,
"accessCodeLifespanUserAction" : 300,
"accessCodeLifespanLogin" : 1800,
"actionTokenGeneratedByAdminLifespan" : 43200,
"actionTokenGeneratedByUserLifespan" : 300,
"enabled" : true,
"sslRequired" : "external",
"registrationAllowed" : false,
"registrationEmailAsUsername" : false,
"rememberMe" : true,
"verifyEmail" : false,
"loginWithEmailAllowed" : true,
"duplicateEmailsAllowed" : false,
"resetPasswordAllowed" : false,
"editUsernameAllowed" : false,
"bruteForceProtected" : false,
"permanentLockout" : false,
"maxFailureWaitSeconds" : 900,
"minimumQuickLoginWaitSeconds" : 60,
"waitIncrementSeconds" : 60,
"quickLoginCheckMilliSeconds" : 1000,
"maxDeltaTimeSeconds" : 43200,
"failureFactor" : 30,
"defaultRoles" : [ "uma_authorization", "offline_access" ],
"requiredCredentials" : [ "password" ],
"passwordPolicy" : "hashIterations(20000)",
"otpPolicyType" : "totp",
"otpPolicyAlgorithm" : "HmacSHA1",
"otpPolicyInitialCounter" : 0,
"otpPolicyDigits" : 6,
"otpPolicyLookAheadWindow" : 1,
"otpPolicyPeriod" : 30,
"otpSupportedApplications" : [ "FreeOTP", "Google Authenticator" ],
"browserSecurityHeaders" : {
"contentSecurityPolicyReportOnly" : "",
"xContentTypeOptions" : "nosniff",
"xRobotsTag" : "none",
"xFrameOptions" : "SAMEORIGIN",
"xXSSProtection" : "1; mode=block",
"contentSecurityPolicy" : "frame-src 'self'",
"strictTransportSecurity" : "max-age=31536000; includeSubDomains"
},
"smtpServer" : { },
"eventsEnabled" : false,
"eventsListeners" : [ "jboss-logging" ],
"enabledEventTypes" : [ ],
"adminEventsEnabled" : false,
"adminEventsDetailsEnabled" : false,
"internationalizationEnabled" : false,
"supportedLocales" : [ ],
"browserFlow" : "browser",
"registrationFlow" : "registration",
"directGrantFlow" : "direct grant",
"resetCredentialsFlow" : "reset credentials",
"clientAuthenticationFlow" : "clients",
"dockerAuthenticationFlow" : "docker auth",
"attributes" : {
"_browser_header.xXSSProtection" : "1; mode=block",
"_browser_header.xFrameOptions" : "SAMEORIGIN",
"_browser_header.strictTransportSecurity" : "max-age=31536000; includeSubDomains",
"permanentLockout" : "false",
"quickLoginCheckMilliSeconds" : "1000",
"displayName" : "Keycloak",
"_browser_header.xRobotsTag" : "none",
"maxFailureWaitSeconds" : "900",
"minimumQuickLoginWaitSeconds" : "60",
"displayNameHtml" : "<div class=\"kc-logo-text\"><span>Keycloak</span></div>",
"failureFactor" : "30",
"actionTokenGeneratedByUserLifespan" : "300",
"maxDeltaTimeSeconds" : "43200",
"_browser_header.xContentTypeOptions" : "nosniff",
"offlineSessionMaxLifespan" : "5184000",
"actionTokenGeneratedByAdminLifespan" : "43200",
"_browser_header.contentSecurityPolicyReportOnly" : "",
"bruteForceProtected" : "false",
"_browser_header.contentSecurityPolicy" : "frame-src 'self'",
"waitIncrementSeconds" : "60",
"offlineSessionMaxLifespanEnabled" : "false"
},
"userManagedAccessAllowed" : false
} ]
我尝试多次总是从一个干净的环境中重新安装,结果总是相同的,一个循环访问主控制台。即使在特权模式下运行 POD / 容器也有相同的结果。
有人可以帮助我检查我做错了什么吗?
先谢谢你了。
共有3个答案
模板创建的路由具有重新加密的 TLS 终止类型。我们将其更改为直通,它起作用了。
您是否正在使用 redis 或其他会话缓存机制?
jboss中有一个关于无限重定向的问题,当您在具有多个前端网关的环境中使用keycloak时,这个问题就会出现。另一个bug的解决方案的链接也贴在那里。
我希望您使用了正确的模板。如果您没有使用正确的模板 - 您最终可能会遇到 HTTPS 重定向问题。而且您不能简单地在(pod 的)端口 8080 上使用 HTTPS。端口 8080 仅适用于 HTTP 流量。
https://github.com/jboss-dockerfiles/keycloak/blob/master/openshift-examples/keycloak-https.json
谢谢
-
最近从Laravel 6升级到Laravel 7,我遇到的问题是,当我使用url /admin它应该重定向到管理员登录页面这也适用于管理员限制页面,如果用户没有登录。我不确定是否需要更改web.php文件或登录控制器中的路由。 登录控制器
-
控制台运行在具有nova-dashboard这一服务器角色的节点上。 向这个云服务的管理员咨询能登录控制台的主机名,IP地址,账号和密码。 打开一个启用了JavaScript和Cookies的浏览器。 注意: 如果要使用VNC客户端,你的浏览器需要支持HTML5 Canvas和HTML5 WebSockets。VNC浏览器基于noVNC。详情请查阅noVNC: HTML5 VNC Client。想
-
SonataUserBundle SonataUserBundle是sonata项目中有关用户管理的部分,它其实是集成了FOS/UserBundle组件(感兴趣可以去git上找,但个人觉得直接用SonataUserBundle就够了)并增添了一些功能,使用SonataUserBundle需要安装如下扩展,执行: [root@centos7vm mywebsite]# composer requi
-
我的目标是添加一个自定义登录页面,以避免对Spring批处理管理控制台进行未经授权的访问。我设置了以下配置:
-
我刚刚安装了一个新的带有 docker 的 centos 服务器 我可以使用命令oc cluster up启动openshift服务器 这给出了输出 oc版本提供了输出 但是当我试图通过https://master.ouatrahim.com:8443/访问Web控制台时,我一直得到一个超文本传输协议重定向到127.0.0.1 希望有人能帮我解决这个
-
我正在将DNN应用程序从07.00.02升级到07.03.04并在安装后将所有门户重定向到登录页面。所有门户都配置有一个登陆页面,该页面被配置为允许“所有用户”角色视图访问。还有人在升级后遇到过这个问题吗? 2015-02-05 05:45:01 127.0.0.1 GET/-80-127.0.0.1 Mozilla/5.0+(Windows+NT+6.3;+WOW64)+AppleWebKit/

