This project is no longer maintained
March 2020 Update: Please go see the amazing Pysa tutorial that should get you up to speed finding security vulnerabilities in your Python codebase.
Pyre from Facebook is an amazing project that has a bright future and many smart people working on it.I would suggest, if you don't know that much about program analysis, that you understand how PyT works before diving into Pyre. Along with the README's in most directories, there are the original Master's Thesis and some slides.With that said, I am happy to review pull requests and give you write permissions if you make more than a few.
There were a lot of great contributors to this project, I plan on working on other projects like detect-secrets and others (e.g. Pyre eventually) in the future if you'd like to work together more :)
If you are a security engineer with e.g. a Python codebase without type annotations, that Pyre won't handle, I would suggest you replace your sinks with a secure wrapper (something like defusedxml), and alert off any uses of the standard sink. You can use Bandit to do this since dataflow analysis is not required, but you will have to trim it a lot, due to the high false-positive rate.
Python Taint
Static analysis of Python web applications based on theoretical foundations (Control flow graphs, fixed point, dataflow analysis)
Features
- Detect command injection, SSRF, SQL injection, XSS, directory traveral etc.
- A lot of customisation possible
For a look at recent changes, please see the changelog.
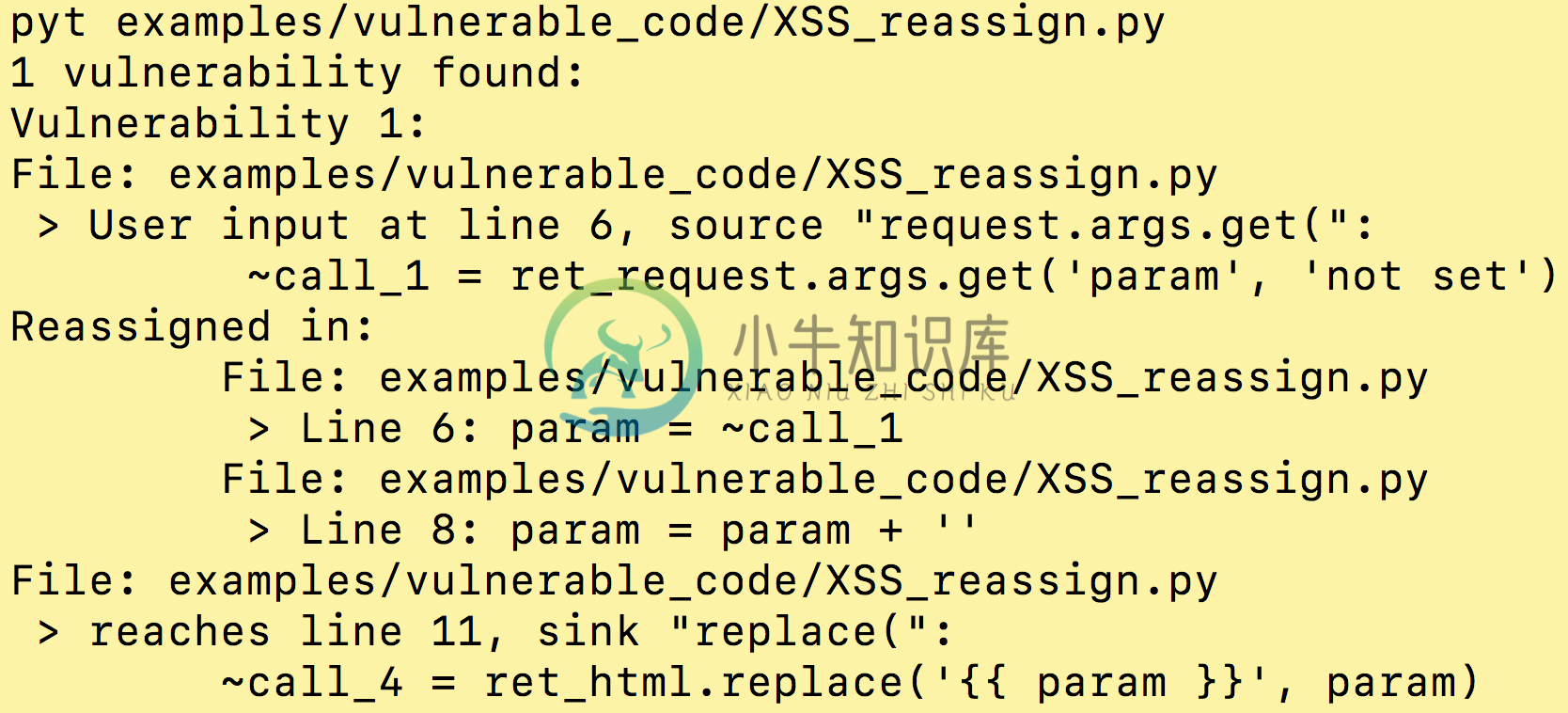
Example usage and output:
Install
Before continuing, make sure you have python3.6 or 3.7 installed.
pip install python-taint
✨��✨
PyT can also be installed from source. To do so, clone the repo, and then run:
python3 setup.py install
How it Works
Soon you will find a README.rst in every directory in the pyt/ folder, start here.
How to Use
- Choose a web framework
The -a option determines which functions will have their arguments tainted, by default it is Flask.
- (optional) Customize source and sink information
Use the -t option to specify sources and sinks, by default this file is used.
- (optional) Customize which library functions propagate taint
For functions from builtins or libraries, e.g. url_for or os.path.join, use the -m option to specify whether or not they return tainted values given tainted inputs, by default this file is used.
Usage
usage: python -m pyt [-h] [-a ADAPTOR] [-pr PROJECT_ROOT]
[-b BASELINE_JSON_FILE] [-j] [-t TRIGGER_WORD_FILE]
[-m BLACKBOX_MAPPING_FILE] [-i] [-o OUTPUT_FILE]
[--ignore-nosec] [-r] [-x EXCLUDED_PATHS]
[--dont-prepend-root] [--no-local-imports]
targets [targets ...]
required arguments:
targets source file(s) or directory(s) to be scanned
important optional arguments:
-a ADAPTOR, --adaptor ADAPTOR
Choose a web framework adaptor: Flask(Default),
Django, Every or Pylons
-t TRIGGER_WORD_FILE, --trigger-word-file TRIGGER_WORD_FILE
Input file with a list of sources and sinks
-m BLACKBOX_MAPPING_FILE, --blackbox-mapping-file BLACKBOX_MAPPING_FILE
Input blackbox mapping file
optional arguments:
-pr PROJECT_ROOT, --project-root PROJECT_ROOT
Add project root, only important when the entry file
is not at the root of the project.
-b BASELINE_JSON_FILE, --baseline BASELINE_JSON_FILE
Path of a baseline report to compare against (only
JSON-formatted files are accepted)
-j, --json Prints JSON instead of report.
-i, --interactive Will ask you about each blackbox function call in
vulnerability chains.
-o OUTPUT_FILE, --output OUTPUT_FILE
Write report to filename
--ignore-nosec Do not skip lines with # nosec comments
-r, --recursive Find and process files in subdirectories
-x EXCLUDED_PATHS, --exclude EXCLUDED_PATHS
Separate files with commas
--dont-prepend-root In project root e.g. /app, imports are not prepended
with app.*
--no-local-imports If set, absolute imports must be relative to the
project root. If not set, modules in the same
directory can be imported just by their names.
Usage from Source
Using it like a user python3 -m pyt examples/vulnerable_code/XSS_call.py
Running the tests python3 -m tests
Running an individual test file python3 -m unittest tests.import_test
Running an individual test python3 -m unittest tests.import_test.ImportTest.test_import
Contributions
Join our slack group: https://pyt-dev.slack.com/ - ask for invite: mr.thalmann@gmail.com
Virtual env setup guide
Create a directory to hold the virtual env and project
mkdir ~/a_folder
cd ~/a_folder
Clone the project into the directory
git clone https://github.com/python-security/pyt.git
Create the virtual environment
python3 -m venv ~/a_folder/
Check that you have the right versions
python3 --version sample output Python 3.6.0
pip --version sample output pip 9.0.1 from /Users/kevinhock/a_folder/lib/python3.6/site-packages (python 3.6)
Change to project directory
cd pyt
In the future, just type source ~/a_folder/bin/activate to start developing.
-
订阅 Python全栈白宝书-零基础入门篇 可报销!白嫖入口-请点击我。推荐他人订阅,可获取扣除平台费用后的35%收益,文末名片加V! 说明:该文属于 Python全栈白宝书专栏,免费阶段订阅数量4300+,购买任意白宝书体系化专栏可加入TFS-CLUB 私域社区。 福利:加入社区的小伙伴们,除了可以获取博主所有付费专栏的阅读权限之外,还有机会加入 星荐官共赢计划
-
WSL安装 WSL可在微软应用商店中下载。 创建账号密码 打开Ubuntu会让你创建用户名和密码。 装mediapipe流程 关于这部分流程可以查看这个博主的流程 https://blog.csdn.net/qq_36818449/article/details/103879399 但是在照着博主做的过程中注意,Bazel的版本要是1.1.0的,因为mediapipe现在最多支持1.1.0的Baz
-
有时候需要将一个python文件添加到linux命令中去执行,更快捷方便。 在终端下面执行python: $ chmod a+rx test.py #设置为可执行文件 $ sudo mv test.py /usr/local/bin/py-test-command #添加到命令目录 $ sudo chown root:root /usr/local/bin/py-test-command #更改
-
报错: Fatal error in launcher: Unable to create process using '"C:\Python37\python.exe" "C:\Python37\Scripts\pip.exe" -v': ??????????? 解决办法: 用你的python命令(python或者python3)来运行pip python3 -m pip -V
-
关于Generator expression must be parenthesized out报错或者Error creating Django application: Error on python side. Exit code: 1的解决办法 如果没有猜错的话 ,你的python解释器是3.7 下载的django1.1之类的版本 他们不兼容 所以无法生成应用 !!! 坑死我
-
问题内容: 为什么以下代码在Python中表现异常? 我正在使用Python 2.5.2。尝试使用某些不同版本的Python,Python 2.3.3似乎在99到100之间显示了上述行为。 基于以上所述,我可以假设Python是内部实现的,因此“小”整数的存储方式与大整数的存储方式不同,并且is运算符可以分辨出这种差异。为什么要泄漏抽象?当我事先不知道它们是否为数字时,比较两个任意对象以查看它们是
-
问题内容: 我在文件中有此: 我编写了以下脚本来打印所有数据: 但是,该程序会引发异常: 如何解析并提取其值? 问题答案: 你的数据不是有效的格式。你有什么时候应该拥有: 用于JSON数组,在Python中称为 用于JSON对象,在Python中称为 JSON文件的外观如下: 然后,你可以使用你的代码: 有了数据,你现在还可以找到类似的值: 试试看,看看是否有意义。
-
问题内容: 如何在Python3中将输入转义到MySQL数据库?我正在使用PyMySQL,并且工作正常,但是当我尝试执行以下操作时: 如果字符串具有或,则它将不起作用。我也尝试过: 问题在于该库(PyMySQL)使用了Python2.x的格式语法,该语法不再起作用。我也发现了这个可能的解决方案 在这里,但我不知道在何处添加此代码。这就是我得到的一切: 编辑:我解决了!在PyMySQL中,正确的方法
-
问题内容: 我想知道在Python应用程序中导入包的首选方法。我有一个这样的包结构: project.app1.views进口project.app1.models和project.app2.models。我想到有两种方法可以做到这一点。 绝对进口: 或具有明确的相对导入,如在Python 2.5中使用PEP 328引入的那样: 什么是最pythonic的方式做到这一点? 问题答案: 绝对进口。从
-
问题内容: 在Python中,该函数允许您迭代一系列(索引,值)对。例如: 用Java有什么办法吗? 问题答案: 对于实现接口的集合,您可以调用方法以获取。迭代器(还有其他方法)有两种方法- ,以获得索引;和,以获取值(与其他迭代器一样)。 因此,上述Python的Java等效项可能是: 与Python一样,它输出:
-
问题内容: 我想从网络摄像头捕获单个图像并将其保存到磁盘。我想用Java或Python(最好是Java)做到这一点。我想要在64位Win7和32位Linux上都可以使用的东西。 编辑:我使用Python 3.x,而不是2.x 因为在其他地方我都看到这个问题,使人们设法感到困惑,所以我将明确说明一些事情: 我不想使用处理 除上述语言外,我不想使用任何其他语言 我确实想以任何方式,形状或形式在屏幕上显
-
问题内容: 我知道(其中e是一个异常)会打印发生的异常,但是,我试图找到与Java等效的python,它可以将异常确切地跟踪到发生的那一行,并打印出整个轨迹。 谁能告诉我Python 的等效功能吗? 问题答案: 在块内执行此操作时,它将自动使用当前异常。有关更多信息,请参见http://docs.python.org/library/traceback.html。
-
问题内容: 在过去的两年中,我一直在编写Java,现在,我开始用python(另外)进行编写。 问题是,当我查看我的Python代码时,似乎有人试图将Java代码转换为python格式,但结果却很糟糕,因为- python不是Java。 关于如何摆脱“用Python编写Java”模式的任何技巧? 谢谢! 问题答案: 您可能会考虑将自己沉浸在Python范例中。最好的方法是首先了解他们的知识,然后通