Serverless IAM Roles Per Function Plugin
A Serverless plugin to easily define IAM roles per function via the use of iamRoleStatements at the function definition block.
Installation
npm install --save-dev serverless-iam-roles-per-function
Or if you want to try out the next upcoming version:
npm install --save-dev serverless-iam-roles-per-function@next
Add the plugin to serverless.yml:
plugins:
- serverless-iam-roles-per-function
Note: Node 6.10 or higher runtime required.
Usage
Define iamRoleStatements definitions at the function level:
functions:
func1:
handler: handler.get
iamRoleStatementsName: my-custom-role-name #optional custom role name setting instead of the default generated one
iamRoleStatements:
- Effect: "Allow"
Action:
- dynamodb:GetItem
Resource: "arn:aws:dynamodb:${self:provider.region}:*:table/mytable"
...
func2:
handler: handler.put
iamRoleStatements:
- Effect: "Allow"
Action:
- dynamodb:PutItem
Resource: "arn:aws:dynamodb:${self:provider.region}:*:table/mytable"
...
The plugin will create a dedicated role for each function that has an iamRoleStatements definition. It will include the permissions for create and write to CloudWatch logs, stream events and if VPC is defined: AWSLambdaVPCAccessExecutionRole will be included (as is done when using iamRoleStatements at the provider level).
if iamRoleStatements are not defined at the function level default behavior is maintained and the function will receive the global iam role. It is possible to define an empty iamRoleStatements for a function and then the function will receive a dedicated role with only the permissions needed for CloudWatch and (if needed) stream events and VPC. Example of defining a function with empty iamRoleStatements and configured VPC. The function will receive a custom role with CloudWatch logs permissions and the policy AWSLambdaVPCAccessExecutionRole:
functions:
func1:
handler: handler.get
iamRoleStatements: []
vpc:
securityGroupIds:
- sg-xxxxxx
subnetIds:
- subnet-xxxx
- subnet-xxxxx
By default, function level iamRoleStatements override the provider level definition. It is also possible to inherit the provider level definition by specifying the option iamRoleStatementsInherit: true:
serverless >= v2.24.0
provider:
name: aws
iam:
role:
statements:
- Effect: "Allow"
Action:
- xray:PutTelemetryRecords
- xray:PutTraceSegments
Resource: "*"
...
functions:
func1:
handler: handler.get
iamRoleStatementsInherit: true
iamRoleStatements:
- Effect: "Allow"
Action:
- dynamodb:GetItem
Resource: "arn:aws:dynamodb:${self:provider.region}:*:table/mytable"
serverless < v2.24.0
provider:
name: aws
iamRoleStatements:
- Effect: "Allow"
Action:
- xray:PutTelemetryRecords
- xray:PutTraceSegments
Resource: "*"
...
functions:
func1:
handler: handler.get
iamRoleStatementsInherit: true
iamRoleStatements:
- Effect: "Allow"
Action:
- dynamodb:GetItem
Resource: "arn:aws:dynamodb:${self:provider.region}:*:table/mytable"
The generated role for func1 will contain both the statements defined at the provider level and the ones defined at the function level.
If you wish to change the default behavior to inherit instead of override it is possible to specify the following custom configuration:
custom:
serverless-iam-roles-per-function:
defaultInherit: true
Role Names
The plugin uses a naming convention for function roles which is similar to the naming convention used by the Serverless Framework. Function roles are named with the following convention:
<service-name>-<stage>-<function-name>-<region>-lambdaRole
AWS has a 64 character limit on role names. If the default naming exceeds 64 chars the plugin will remove the suffix: -lambdaRole to shorten the name. If it still exceeds 64 chars an error will be thrown containing a message of the form:
auto generated role name for function: ${functionName} is too long (over 64 chars).
Try setting a custom role name using the property: iamRoleStatementsName.
In this case you should set the role name using the property iamRoleStatementsName. For example:
functions:
func1:
handler: handler.get
iamRoleStatementsName: my-custom-role-name
iamRoleStatements:
- Effect: "Allow"
Action:
- dynamodb:GetItem
Resource: "arn:aws:dynamodb:${self:provider.region}:*:table/mytable"
...
PermissionsBoundary
Define iamPermissionsBoundary definitions at the function level:
functions:
func1:
handler: handler.get
iamPermissionsBoundary: !Sub arn:aws:iam::xxxxx:policy/your_permissions_boundary_policy
iamRoleStatementsName: my-custom-role-name
iamRoleStatements:
- Effect: "Allow"
Action:
- sqs:*
Resource: "*"
...
You can set permissionsBoundary for all roles with iamGlobalPermissionsBoundary in custom:
custom:
serverless-iam-roles-per-function:
iamGlobalPermissionsBoundary: !Sub arn:aws:iam::xxxx:policy/permissions-boundary-policy
For more information, see Permissions Boundaries.
Contributing
Contributions are welcome and appreciated.
- Before opening a PR it is best to first open an issue. Describe in the issue what you want you plan to implement/fix. Based on the feedback in the issue, you should be able to plan how to implement your PR.
- Once ready, open a PR to contribute your code.
- To help updating the CHANGELOG.md file, we use standard-version. Make sure to use conventional commit messages as specified at: https://www.conventionalcommits.org/en/v1.0.0/.
- Update the release notes at CHANGELOG.md and bump the version by running:
npm run release - Examine the CHANGELOG.md and update if still required.
- Don't forget to commit the files modified by
npm run release(we have the auto-commit option disabled by default). - Once the PR is approved and merged into master, travis-ci will automatically tag the version you created and deploy to npmjs under the
nexttag. You will see your version deployed at: https://www.npmjs.com/package/serverless-iam-roles-per-function?activeTab=versions. - Test your deployed version by installing with the
nexttag. For example:npm install --save-dev serverless-iam-roles-per-function@next
Publishing a Production Release (Maintainers)
Once a contributed PR (or multiple PRs) have been merged into master, there is need to publish a production release, after we are sure that the release is stable. Maintainers with commit access to the repository can publish a release by merging into the release branch. Steps to follow:
Verify that the current deployed pre-release version under the
nexttag in npmjs is working properly. Usually, it is best to allow thenextversion to gain traction a week or two before releasing. Also, if the version solves a specific reported issue, ask the community on the issue to test out thenextversion.Make sure the version being used in master hasn't been released. This can happen if a PR was merged without bumping the version by running
npm run release. If the version needs to be advanced, open a PR to advance the version as specified here.Open a PR to merge into the
releasebranch. Use as a base thereleasebranch and compare thetagversion torelease. For example: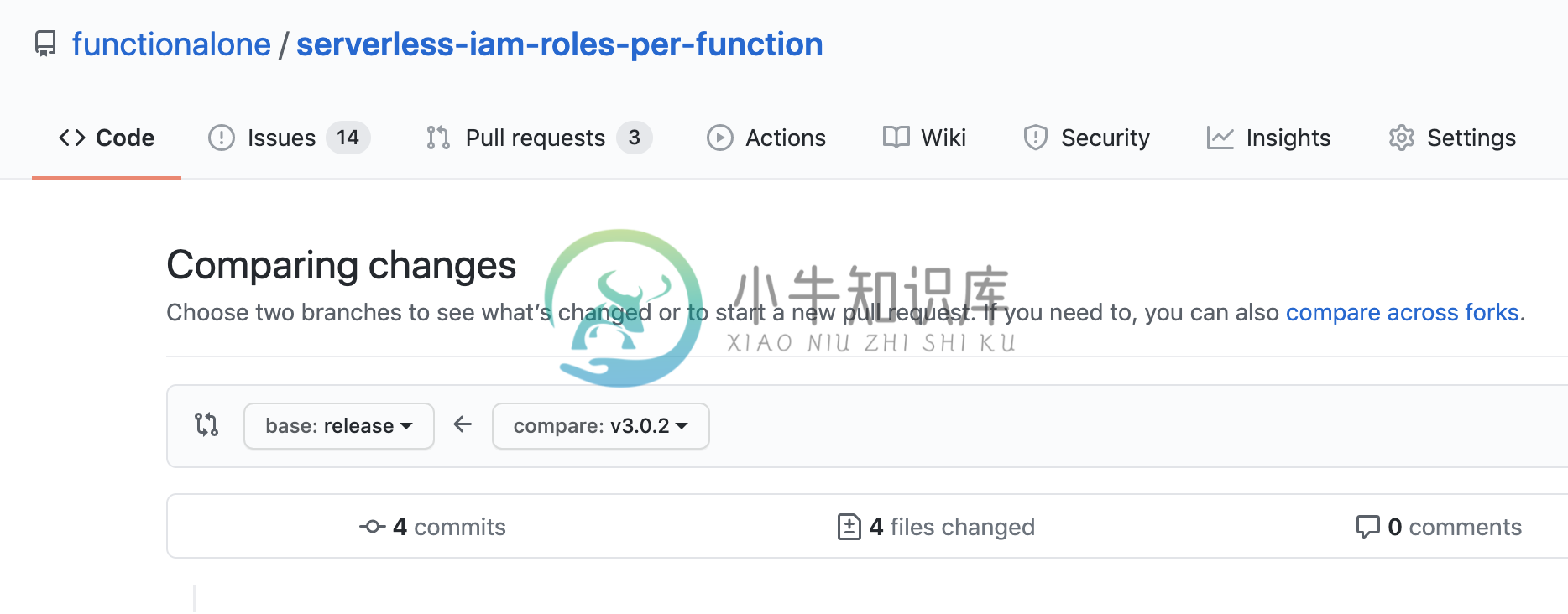
Once approved by another maintainer, merge the PR.
Make sure to check after the Travis CI build completes that the release has been published to the
latesttag on nmpjs.
More Info
Introduction post:Serverless Framework: Defining Per-Function IAM Roles
Note: Serverless Framework provides support for defining custom IAM roles on a per function level through the use of the role property and creating CloudFormation resources, as documented here. This plugin doesn't support defining both the role property and iamRoleStatements at the function level.
-
Serverless Single Page Apps Fast, Scalable, and Available Intro[编辑] Avoid Yaks(yak shaving) Move Faster with Tests(work with confidence) TDD:Red-Green-Refactor Starting Simple[编辑] Benefits of a Server
-
Per-cpu 变量是一项内核特性。从它的名字你就可以理解这项特性的意义了。我们可以创建一个变量,然后每个 CPU 上都会有一个此变量的拷贝。本节我们来看下这个特性,并试着去理解它是如何实现以及工作的。 内核提供了一个创建 per-cpu 变量的 API - DEFINE_PER_CPU 宏: #define DEFINE_PER_CPU(type, name) \ DEFINE_
-
IAM = Identity and Access Management IAM 是一个基于 Go 语言开发的身份识别与访问管理系统,用于对资源访问进行授权。最新稳定版本为:v1.6.2,建议基于稳定版安装测试。企业级的 Go 语言实战项目(可作为Go项目开发脚手架) 这里需要注意: 如果你是极客时间《Go 语言项目开发实战》专栏的读者,请使用 v1.1.0 版本(tag) 如果你是图书《从零构建
-
云原生应用开发 回顾过去二十年,应用开发有以下几个显著的特点: 以应用服务器为中心,典型应用服务器包括 tomcat,JBoss,WebLogic,WebSphere,应用服务器提供了丰富的技术堆栈和系统构建范式,对应用开发人员友好 JavaEE/Spring,JavaEE/Spring 是应用开发的基本技能,这项技能有广泛的开发者基础,过去二十年中 JavaEE/Spring 的技术发展/版本的
-
The Serverless Framework (无服务器架构)允许你自动扩展、按执行付费、将事件驱动的功能部署到任何云。 目前支持 AWS Lambda、Apache OpenWhisk、Microsoft Azure,并且正在扩展以支持其他云提供商。 Serverless 降低了维护应用程序的总成本,能够更快地构建更多逻辑。它是一个命令行工具,提供脚手架、工作流自动化和开发部署无服务器架构的最佳实践。它也可以通过插件完全扩展。
-
Serverless Step Functions This is the Serverless Framework plugin for AWS Step Functions. Requirement Serverless Framework v2.32.0 or later is required. TOC Install Setup Adding a custom name for a st
-
Azure Functions Serverless Plugin This plugin enables Azure Functions support within the Serverless Framework. Quickstart Pre-requisites Node.js 8.x or above Serverless CLI v1.9.0+. You can run npm i

