Java错误,如何知道丢失的证书是哪一个?“找不到请求目标的有效证书路径”
我试图通过SSL加载一个页面,但出现以下错误:
PKIX路径构建失败:sun.security.provider.certpath.SunCertPathBuilderExctive:无法找到请求目标的有效认证路径
当然,我对此进行了研究,它与我下载的java发行版中没有包含的页面证书有关。以下是我正在加载的站点的Certifcate层次结构:
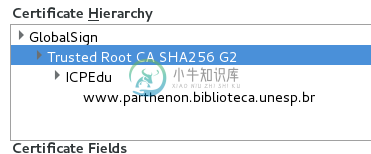
第一个(全球符号)当然包括在系统中。但什么是“可信根CA SHA256 G2”?Firefox说它的签名是GlobalSign。还有,ICPEdu可能是丢失的证书吗?如果是这样,我如何将其添加到java代码中的受信任证书列表中?
但是等一下。。。既然GlobalSign是受信任的,那么下面的每个证书不也应该受信任吗?
正如答案所指出的,下面是ssl调试:
Certificate Extensions: 9
[1]: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://secure.globalsign.com/cacert/icpedusha2g2.crt
,
accessMethod: ocsp
accessLocation: URIName: http://ocsp2.globalsign.com/icpedusha2g2
]
]
[2]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 95 F0 A4 84 1A A7 5C 20 36 A6 C5 08 D7 65 42 02 ......\ 6....eB.
0010: E5 77 68 E3 .wh.
]
]
[3]: ObjectId: 2.5.29.19 Criticality=false
BasicConstraints:[
CA:false
PathLen: undefined
]
[4]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.globalsign.com/gs/icpedusha2g2.crl]
]]
[5]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.2]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 26 68 74 74 70 73 3A 2F 2F 77 77 77 2E 67 6C .&https://www.gl
0010: 6F 62 61 6C 73 69 67 6E 2E 63 6F 6D 2F 72 65 70 obalsign.com/rep
0020: 6F 73 69 74 6F 72 79 2F ository/
]] ]
]
[6]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
[7]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
[8]: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: www.parthenon.biblioteca.unesp.br
DNSName: parthenon.biblioteca.unesp.br
]
[9]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 6D BE 57 72 E3 B5 BD A2 0E 16 E3 A9 2F 8B E7 87 m.Wr......../...
0010: F1 4B 27 75 .K'u
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 2D 83 5B 63 56 82 77 74 FB EF 40 C1 7A 88 9B 1B -.[cV.wt..@.z...
0010: 34 37 79 4E 28 A4 79 18 69 25 FE 52 90 B4 79 B7 47yN(.y.i%.R..y.
0020: 90 00 58 CE 21 E6 96 BC E7 5B C3 5D 41 38 51 5E ..X.!....[.]A8Q^
0030: B5 DA D2 EA F6 44 83 FA B7 A8 66 90 77 C9 96 3D .....D....f.w..=
0040: 72 AE 05 5C F2 19 AE 36 43 F6 A5 DF E2 E5 F8 50 r..\...6C......P
0050: D3 CC EF AE 79 29 19 F6 F8 63 C0 26 E9 0C FA 86 ....y)...c.&....
0060: 30 1D BF 00 69 C8 E9 B5 B6 16 BE 6B 5F 63 5B AD 0...i......k_c[.
0070: F5 B4 18 82 0C 53 ED 36 AB 38 61 8B 80 C9 8C 62 .....S.6.8a....b
0080: E6 20 E3 CB 5A 2A 91 C2 CA 6A BE 31 B6 CB 65 57 . ..Z*...j.1..eW
0090: 33 47 43 9A B4 33 5B 45 D9 5E ED C6 7C 2B 0D B3 3GC..3[E.^...+..
00A0: E6 4C 5F 85 EF D0 BE CD 02 1B 6B C1 06 2F 7B F6 .L_.......k../..
00B0: C0 B7 C4 68 F1 F6 92 2B A4 B6 85 08 32 7C 8D 9F ...h...+....2...
00C0: 34 7D 08 5B B4 05 51 C8 E6 C4 29 86 04 32 FA 2B 4..[..Q...)..2.+
00D0: 18 42 56 43 88 DB EE 32 5F CE 8D 88 5E 91 C1 72 .BVC...2_...^..r
00E0: CB 0F FE F3 CA 55 D3 A4 40 57 E0 13 03 3F C9 16 .....U..@W...?..
00F0: 1F FC 31 28 CB 68 06 9F 0F 3A D2 3A 91 65 B2 D8 ..1(.h...:.:.e..
]
***
%% Invalidated: [Session-1, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA]
main, SEND TLSv1 ALERT: fatal, description = certificate_unknown
main, WRITE: TLSv1 Alert, length = 2
main, called closeSocket()
main, handling exception: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
main, called close()
main, called closeInternal(true)
Exception in thread "main" javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
共有2个答案
我认为对您来说最好的事情是查看从服务器发送到客户机的确切内容。您可以将证书链发送到浏览器,并使用openSSL或更好的方式通过在线解析器对其进行解析,如:http://developerutils.com/X509CertificateDecoder.php
您可以向服务器日志记录选项中添加:-Djavax。网debug=ssl,handshake查看整个握手过程。
这应该有助于你弄清楚到底发生了什么。
关于链本身:如果发送了一个链,并且链的根在受信任的CA列表中,则链的其余部分是受信任的,除非链中的一个证书被吊销或过期。
服务器www.parthenon.biblioteca.unesp.br没有在握手中发送其中间证书。
服务器管理员可以通过在服务器配置中提供缺少的中间证书来纠正此问题。
-
谢谢你,我很乐意提供任何其他需要的细节。
-
在Keycloak服务器控制台中 我已成功测试与 Windows Active Directory 服务器的连接 - 正常 但是在测试验证时继续接收错误消息 服务器控制台输出:验证器异常:PKIX 路径构建失败:sun.security.provider.certpath.SunCertPathBuilder异常:找不到到请求目标的有效证书路径 但仍然存在相同的错误。
-
我在Apache Tomcat7上有一个web应用程序,我的web应用程序上有不可信的证书。我的web应用程序必须与另一个使用HTTPS的web应用程序通信。然而,我总是遇到这样一个例外: 连接失败:javax.net.ssl.sslhandShakeException:sun.security.validator.validatoreXception:PKIX路径构建失败:sun.securit
-
我试图访问我的应用程序中的网址,但我得到了这个错误。 我尝试应用所有这些修复,但没有成功:http://www.mkyong.com/webservices/jax-ws/suncertpathbuilderexception-unable-to-find-valid-certification-path-to-requested-target/ 很快,它需要运行InstallCert应用程序(j
-
我刚刚安装了最新的Android Studio,我得到了标题中的错误;我尝试了互联网上的许多解决方案,但都不起作用。 所以请你帮我修一下好吗? 我收到此错误: 该项目是Android Studio中的基本项目示例。
-
我最近为我的maven repo(Apache代理背后的人工制品)切换到了letsencrypt证书。通过浏览器访问回购协议工作正常,证书没有问题(下面的屏幕截图)。 如果我手动将证书导入到java密钥库中,它也可以工作。 但是根据这个SO问题,Java应该接受以8u101开头的lets加密证书。 我总是遇到这样的例外:

