如何在部署过程中使用Azure密钥库传递安全参数值?
我有一个用于在Azure管道中部署Service Fabric集群的ARM模板:
- task: AzureResourceManagerTemplateDeployment@3
displayName: 'Deploy SF cluster'
inputs:
deploymentScope: 'Resource Group'
subscriptionId: '${{ parameters.SubscriptionId }}'
azureResourceManagerConnection: '${{ parameters.ArmConnection }}'
action: 'Create Or Update Resource Group'
resourceGroupName: '${{ parameters.ResourceGroupName }}'
location: 'West Europe'
templateLocation: 'Linked artifact'
csmFile: '$(Build.SourcesDirectory)/pipelines/templates/sfcluster.json'
csmParametersFile: '$(Build.SourcesDirectory)/pipelines/templates/sfcluster-params.json'
overrideParameters: '-certificateThumbprint $(Thumbprint) -sourceVaultResourceId $(KeyvaultId) -certificateUrlValue $(SecretId)'
deploymentMode: 'Incremental'
ARM模板工作良好(因为许多天和在5个不同的管道),当我使用:
"osProfile": {
"adminUsername": "RdpUsername",
"adminPassword": "RdpPassword",
"computernamePrefix": "[variables('vmNodeType0Name')]",
"secrets": [
{
"sourceVault": {
"id": "[parameters('sourceVaultResourceId')]"
},
"vaultCertificates": [
{
"certificateStore": "My",
"certificateUrl": "[parameters('certificateUrlValue')]"
}
]
}
]
},
然而,具有硬编码的RDP凭据是一个安全问题,因此我希望在部署期间使用Azure密钥库传递安全参数值
"osProfile": {
"adminUsername": {
"reference": {
"keyVault": {
"id": "[parameters('sourceVaultResourceId')]"
},
"secretName": "RdpUsername"
}
},
"adminPassword": {
"reference": {
"keyVault": {
"id": "[parameters('sourceVaultResourceId')]"
},
"secretName": "RdpPassword"
}
},
"computernamePrefix": "[variables('vmNodeType0Name')]",
"secrets": [
{
"sourceVault": {
"id": "[parameters('sourceVaultResourceId')]"
},
"vaultCertificates": [
{
"certificateStore": "My",
"certificateUrl": "[parameters('certificateUrlValue')]"
}
]
}
]
},
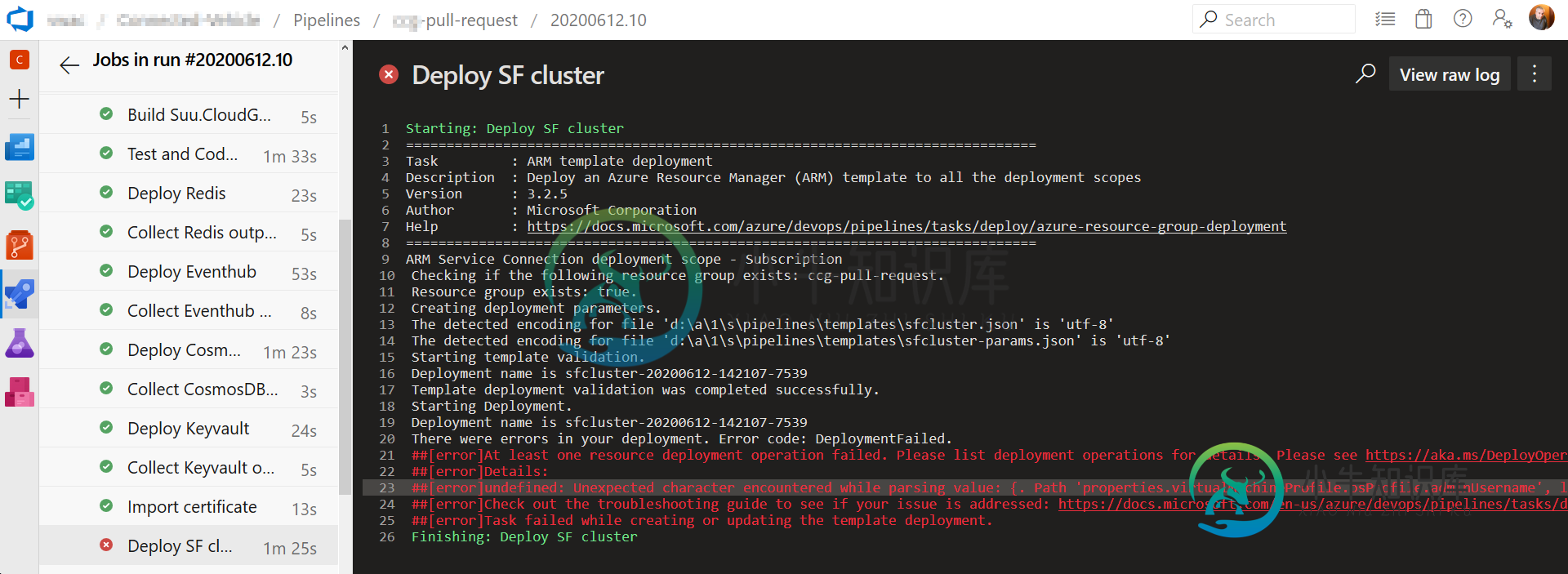
我的ARM模板是基于azure-quickstart-templates/service-fabrice-secure-cluster-5-node-1-nodeType的,正如上面写的那样,使用硬编码值工作。
更新:
这里是我的sfcluster-params.json(但也请注意下面列出的管道任务中的overrideParameters,它填充了Keyvault部署设置的管道变量):
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"clusterName": {
"value": "sfcluster"
}
}
}
# deploy KeyVault by ARM template and output VinHashKey and SF Cluster certificate thumbsprint
- task: AzureResourceManagerTemplateDeployment@3
displayName: 'Deploy Keyvault'
inputs:
deploymentScope: 'Resource Group'
subscriptionId: '${{ parameters.SubscriptionId }}'
azureResourceManagerConnection: '${{ parameters.ArmConnection }}'
action: 'Create Or Update Resource Group'
resourceGroupName: '${{ parameters.ResourceGroupName }}'
location: 'West Europe'
templateLocation: 'Linked artifact'
csmFile: '$(Build.SourcesDirectory)/pipelines/templates/keyvault.json'
csmParametersFile: '$(Build.SourcesDirectory)/pipelines/templates/keyvault-params.json'
deploymentMode: 'Incremental'
# collect outputs from the above ARM task and put them into pipeline vars
- task: ARM Outputs@5
displayName: 'Collect Keyvault output'
inputs:
ConnectedServiceNameSelector: 'ConnectedServiceNameARM'
ConnectedServiceNameARM: '${{ parameters.ArmConnection }}'
resourceGroupName: '${{ parameters.ResourceGroupName }}'
whenLastDeploymentIsFailed: 'fail'
# import the certificate my-self-signed-cert into the Keyvault if it is missing there
- task: AzurePowerShell@5
displayName: 'Import certificate'
inputs:
azureSubscription: '${{ parameters.ArmConnection }}'
ScriptType: 'InlineScript'
azurePowerShellVersion: '3.1.0'
Inline: |
$Cert = Get-AzKeyVaultCertificate -VaultName $(KeyVaultName) -Name my-self-signed-cert
if (!$Cert) {
$Pwd = ConvertTo-SecureString -String MyPassword -Force -AsPlainText
$Base64 = 'MII....gfQ'
$Cert = Import-AzKeyVaultCertificate -VaultName $(KeyVaultName) -Name my-self-signed-cert -CertificateString $Base64 -Password $Pwd
}
# set the pipeline variables Thumbprint and SecretId - needed for SF deployment
echo "##vso[task.setvariable variable=Thumbprint]$($Cert.Thumbprint)"
echo "##vso[task.setvariable variable=SecretId]$($Cert.SecretId)"
# deploy SF cluster by ARM template and use the SF certificate thumbsprint as admin cert
- task: AzureResourceManagerTemplateDeployment@3
displayName: 'Deploy SF cluster'
inputs:
deploymentScope: 'Resource Group'
subscriptionId: '${{ parameters.SubscriptionId }}'
azureResourceManagerConnection: '${{ parameters.ArmConnection }}'
action: 'Create Or Update Resource Group'
resourceGroupName: '${{ parameters.ResourceGroupName }}'
location: 'West Europe'
templateLocation: 'Linked artifact'
csmFile: '$(Build.SourcesDirectory)/pipelines/templates/sfcluster.json'
csmParametersFile: '$(Build.SourcesDirectory)/pipelines/templates/sfcluster-params.json'
overrideParameters: '-certificateThumbprint $(Thumbprint) -sourceVaultResourceId $(KeyvaultId) -certificateUrlValue $(SecretId)'
deploymentMode: 'Incremental'
最后,这里是sfcluster.json-它太大了,不能放在StackOverflow中。
共有1个答案
keyVault引用只能用作参数值-因此在param文件或部署的parameters属性中。不能将其直接用作资源上的属性值。
-
我在大多数文章中读到,需要在Azure中部署应用程序,这样应用程序才能以编程方式访问存储在Azure密钥库中的秘密。 有没有一种方法可以不在azure中部署应用程序,并且仍然能够通过使用客户端id和客户端机密或证书来访问azure密钥库以获取机密?
-
我试图用和部署一个密钥存储库,并在azure devops中创建了一个包含所有秘密的变量组,我在参数文件中使用了以下参数,但是当部署这个参数时,秘密值将存储为$(secret),而不是实际存储在azure devops任务组中的密码。 这是我在密钥库模板中得到的:
-
我想自动部署可变数量的虚拟机(通过副本部署),通过取代密码的密钥保险库秘密。我想为不同的VM使用不同的秘密(例如secret1用于VM1,secret2用于VM2)。根据文档,我需要引用一个带有动态id的秘密https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-manager-keyvault-paramete
-
我正在开发一个将文件上传到Azure存储的.NET应用程序。我正在利用https://azure.microsoft.com/en-us/documentation/articles/storage-encrypt-decrypt-blobs-key-vault/教程中所做的客户端加密 应用程序工作,即,我可以成功地上传一个加密的blob到一个选定的存储帐户和容器。 但是,我对RSA密钥的安全性有

