GoQuorum is an Ethereum-based distributed ledger protocol with transaction/contract privacy and new consensus mechanisms.
GoQuorum is a fork of go-ethereum and is updated in line with go-ethereum releases.
Key enhancements over go-ethereum:
- Privacy - GoQuorum supports private transactions and private contracts through public/private state separation, and utilises peer-to-peer encrypted message exchanges (see Constellation and Tessera) for directed transfer of private data to network participants
- Alternative Consensus Mechanisms - with no need for POW/POS in a permissioned network, GoQuorum instead offers multiple consensus mechanisms that are more appropriate for consortium chains:
- Raft-based Consensus - a consensus model for faster blocktimes, transaction finality, and on-demand block creation
- Istanbul BFT - a PBFT-inspired consensus algorithm with transaction finality, by AMIS.
- Clique POA Consensus - a default POA consensus algorithm bundled with Go Ethereum.
- Peer Permissioning - node/peer permissioning, ensuring only known parties can join the network
- Account Management - GoQuorum introduced account plugins, which allows GoQuorum or clef to be extended with alternative methods of managing accounts including external vaults.
- Pluggable Architecture - allows adding additional features as plugins to the core
geth, providing extensibility, flexibility, and distinct isolation of GoQuorum features. - Higher Performance - GoQuorum offers significantly higher performance throughput than public geth
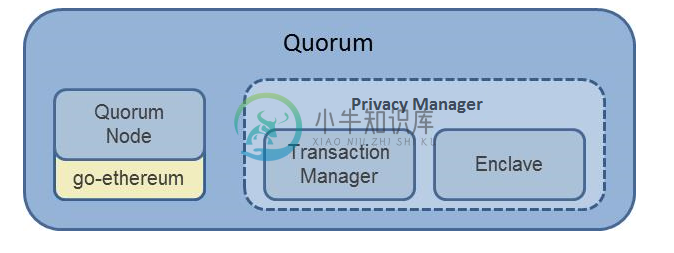
Architecture
The above diagram is very high-level overview of component architecture used by GoQuorum. For more in-depth discussion of the components and how they interact, please refer to lifecycle of a private transaction.
Quickstart
There are several ways to quickly get up and running with GoQuorum. One of the easiest is to use GoQuorum Wizard - a command line tool that allows users to set up a development GoQuorum network on their local machine in less than 2 minutes.
GoQuorum Projects
Check out some of the interesting projects we are actively working on:
- quorum-wizard: Setup a GoQuorum network in 2 minutes!
- quorum-remix-plugin: The GoQuorum plugin for Ethereum's Remix IDE adds support for creating and interacting with private contracts on a GoQuorum network.
- Cakeshop: An integrated development environment and SDK for GoQuorum
- quorum-profiling: Toolset for stress testing & benchmarking GoQuorum networks.
- quorum-examples: GoQuorum demonstration examples
- qubernetes: Deploy GoQuorum on Kubernetes
- quorum-cloud: Tools to help deploy GoQuorum network in a cloud provider of choice
- quorum.js: Extends web3.js to support GoQuorum-specific APIs
- Zero Knowledge on GoQuorum
- ZSL POC and ZSL on GoQuorum
- Anonymous Zether implementation
Official Docker Containers
The official docker containers can be found under https://hub.docker.com/u/quorumengineering/
Third Party Tools/Libraries
The following GoQuorum-related libraries/applications have been created by Third Parties and as such are not specifically endorsed by J.P. Morgan. A big thanks to the developers for improving the tooling around GoQuorum!
- Quorum Blockchain Explorer - a Blockchain Explorer for GoQuorum which supports viewing private transactions
- Quorum-Genesis - A simple CL utility for GoQuorum to help populate the genesis file with voters and makers
- Quorum Maker - a utility to create GoQuorum nodes
- QuorumNetworkManager - makes creating & managing GoQuorum networks easy
- ERC20 REST service - a GoQuorum-supported RESTful service for creating and managing ERC-20 tokens
- Nethereum Quorum - a .NET GoQuorum adapter
- web3j-quorum - an extension to the web3j Java library providing support for the GoQuorum API
- Apache Camel - an Apache Camel component providing support for the GoQuorum API using web3j library. Here is the artcile describing how to use Apache Camel with Ethereum and GoQuorum https://medium.com/@bibryam/enterprise-integration-for-ethereum-fa67a1577d43
Contributing
GoQuorum is built on open source and we invite you to contribute enhancements. Upon review you will be required to complete a Contributor License Agreement (CLA) before we are able to merge. If you have any questions about the contribution process, please feel free to send an email to info@goquorum.com. Please see the Contributors guide for more information about the process.
Reporting Security Bugs
Security is part of our commitment to our users. At GoQuorum we have a close relationship with the security community, we understand the realm, and encourage security researchers to become part of our mission of building secure reliable software. This section explains how to submit security bugs, and what to expect in return.
All security bugs in GoQuorum and its ecosystem (Tessera, Constellation, Cakeshop, ..etc) should be reported by email to security-quorum@consensys.net. Please use the prefix [security] in your subject. This email is delivered to GoQuorum security team. Your email will be acknowledged, and you'll receive a more detailed response to your email as soon as possible indicating the next steps in handling your report. After the initial reply to your report, the security team will endeavor to keep you informed of the progress being made towards a fix and full announcement.
If you have not received a reply to your email or you have not heard from the security team please contact any team member through GoQuorum slack security channel. Please note that GoQuorum slack channels are public discussion forum. When escalating to this medium, please do not disclose the details of the issue. Simply state that you're trying to reach a member of the security team.
Responsible Disclosure Process
GoQuorum project uses the following responsible disclosure process:
- Once the security report is received it is assigned a primary handler. This person coordinates the fix and release process.
- The issue is confirmed and a list of affected software is determined.
- Code is audited to find any potential similar problems.
- If it is determined, in consultation with the submitter, that a CVE-ID is required, the primary handler will trigger the process.
- Fixes are applied to the public repository and a new release is issued.
- On the date that the fixes are applied, announcements are sent to Quorum-announce.
- At this point you would be able to disclose publicly your finding.
Note: This process can take some time. Every effort will be made to handle the security bug in as timely a manner as possible, however it's important that we follow the process described above to ensure that disclosures are handled consistently.
Receiving Security Updates
The best way to receive security announcements is to subscribe to the Quorum-announce mailing list/channel. Any messages pertaining to a security issue will be prefixed with [security].
Comments on This PolicyIf you have any suggestions to improve this policy, please send an email to info@goquorum.com for discussion.
License
The go-ethereum library (i.e. all code outside of the cmd directory) is licensed under theGNU Lesser General Public License v3.0, alsoincluded in our repository in the COPYING.LESSER file.
The go-ethereum binaries (i.e. all code inside of the cmd directory) is licensed under theGNU General Public License v3.0, also includedin our repository in the COPYING file.
Any project planning to use the crypto/secp256k1 sub-module must use the specific secp256k1 standalone library licensed under 3-clause BSD.
-
在《分布式系统之中心副本控制协议(Primary-secondary协议)》 中略微提及到了Quorum,但没有进行详细的阐述,这篇文章将带你走进Quorum. 1. Quorum介绍 首先,先认识发音和基本含义,英[ˈkwɔ:rəm], 美[ˈkwɔrəm, ˈkwor-],n. 法定人数. 在介绍Quorum之前,先对一些概念进行定义:系统中的更新操作定义为 w i w_i wi, i i
-
Quorum (分布式系统) Quorum 机制,是一种分布式系统中常用的,用来保证数据冗余和最终一致性的投票算法,其主要数学思想来源于鸽巢原理。 基于Quorum投票的冗余控制算法 在有冗余数据的分布式存储系统当中,冗余数据对象会在不同的机器之间存放多份拷贝。但是同一时刻一个数据对象的多份拷贝只能用于读或者用于写。 该算法可以保证同一份数据对象的多份拷贝不会被超过两个访问对象读写。 算法来源
-
Quorum,英文字面意思是“法定人数”。指选举时通常要求参与人数必须达到额定的数量,才能成为一个法定有效的选举。这个额定的人数就是Quorum。 计算机世界里,分布式系统的设计中会涉及到许多的协议、机制用来解决可靠性问题、数据一致性问题等,Quorum 机制就是其中的一种。 Quorom 机制,是一种分布式系统中常用的,用来保证数据冗余和最终一致性的投票算法,其主要数学思想来源于鸽巢原理。 什么
-
分布式系统中,一般保存多个数据副本,明显可以提高系统可靠性。并且存储这些数据副本的节点,不仅做容灾用,也可以提供服务,作负载均衡。 这里就涉及到一个数据一致性的问题,也就是各副本间要进行同步,来保持最新的数据。在一些一致性需求不辣么强的场景,比如用户获取某个文章的点赞数,读到未及时同步的脏数据也就无所谓了。 但在一些需要强一致性的场景里,这就比较可怕了。比如你银行卡里笼共就100块钱,第一次取了6
-
WARO协议 WARO(Write All Read one)是一种简单的副本控制协议,当Client请求向某副本写数据时(更新数据),只有当所有的副本都更新成功之后,这次写操作才算成功,否则视为失败。 从这里可以看出两点: ①写操作很脆弱,因为只要有一个副本更新失败,此次写操作就视为失败了。 ②读操作很简单,因为,所有的副本更新成功,才视为更新成功,从而保证所有的副本一致。这样,只需要读任何一个
-
Quorum快速部署,以下操作均在命令行执行。 参考https://docs.goquorum.consensys.net/en/stable/HowTo/GetStarted/Wizard/GettingStarted/ 需要预安装:Node.js/NPM 正式开始 使用NPM安装 npm install -g quorum-wizard 安装完成之后,执行 quorum-wizard 接下
-
环境 Ubuntu18.04 Docker Engine 18.02.0 Docker Compose 1.21+ 引言 quorum examples包含Quorum平台的安装示例,启动由7个独立节点组成的功能齐全的Quorum环境,从这个例子中可以测试以太坊平台的共识、隐私和所有预期功能。 1. 安装docker 参考ubuntu安装、更新docker社区版 2. 安装docker-compo
-
QuorumPeer是zookeeper执行同步,选主过程的线程 主要逻辑: 1.当自己处于 LOOKING状态: 执行lookForLeader() 2.当自己处于OBSERVING状态: 建立一个Observer服务和leader进行同步 3.当自己处于LEADING时: 建立一个Leader服务,处理peer的请求. 4.当自己处于FOLLOWING时:建立一个Follw
-
背景 hdfs单点问题,可能是机器故障,可能是软硬件升级。 解决方案,使用冗余的NameNode做一个热备份。 架构设计 Standby和Active节点之间和JournalNodes通信,当Active节点执行修改时,持久把修改记录记录的JN中。Standby监测,并从JN中读取编辑。 1.如果突然大量的操作会怎么样? 2.JournalNodes如何被监控的? 为了提供快速的故障转移,Stan
-
1.前言 在阅读本文之前请现阅读《etcd的raft实现之log》,笔者的etcd的raft系列通过一个点(就是log)进行展开,能够让读者比较容易的理解etcd的raft实现,解决读者无从下手的难题。 在开始分析之前,先做一些名词解释,在《etcd的raft实现之log》中提到的概念本文就不在重复了: Peer:原意是同龄人或者同辈份的人,在raft中是参与选举和投票的节点,寓意raft节点都是
-
这块内容主要是一个拜占庭的过程。本文掐头去尾,只讲一下在 quorum 中是如何实现拜占庭的,也就是共识接口 Seal() 下向拜占庭发送了一个区块的请求事件开始。请求事件如下: // post block into Istanbul engine go sb.EventMux().Post(istanbul.RequestEvent{ Proposal: block, }) 前言 在说正文之
-
要配置,它需要,而BrokerHosts又需要一个动物园管理员主机。 问题是,如果我有一个zookeeper仲裁(由3个zk服务器组成的集群),我如何配置KafkaSpout以获取仲裁的所有成员,而不是仅1个。因为一个zookeeper服务器可能会停机,整个拓扑将不可用。
-
我开始使用ubuntu和Apache kafka,当我运行bin/zookeeper-server-start . sh config/zookeeper . properties时出现以下问题 :~/Documentos/kafka-0.8.2.1-src$ Error: no se ha encontrado o cargado la clase principal org.apache.zo
-
我们正在尝试使用ZK设置火花高可用性设置。我们有2台机器用于Spark进程的主机,另有3台机器用于Spark从机。Spark主机中的配置在spark-env.sh中如下所示: 其中DEV-SMP-Manager01:2181DEV-SMP-Worker01:2181、DEV-SMP-Worker05:2181是ZK法定人数。它们都在运行。 我们看到了一些与curator相关的错误消息 java.l
-
我刚从Apache网站下载了Kafka2.8.0,我正在尝试使用网站上给出的说明进行设置。但是当我尝试启动zookeper服务器时,我得到了以下错误: 错误:找不到或加载主类org.apache.zookeeper.server.quorum.QuorumPeerMain 我的环境是Windows764位。我试着遵循下面的电子邮件链:Apache电子邮件链。但它仍然有同样的问题。有人能在这方面指导
-
我对卡珊德拉的一致性有疑问。我在集群中有3个Cassandra节点(版本2.0.14.352 ),我使用< b >一致性级别仲裁读取和写入,我的< b >复制因子是3。如果我理解replication_factor " >这个对我来说卡珊德拉应该是一致的,因为2 ^ 2 与相应的表 dataProvider.setValue()内部将给定值放入NavigableMap。dataProvider.s
-
在一个如下的四节点环境中, 如果sentinel monitor的quorum设置为3,则宕机一台后再宕机,此时还剩余两台,存在两个sentinel,两个slave。由于quorum为3,而必须有>=max(quorum, num(sentinels)/2 +1) = max(3,2) = 3个sentinel都同意其中某一个sentinel主持failover,因此此时无sentinel可主持切